Kaspersky's Global Research and Analysis Team (GReAT) has just announced the latest activity of the APT hacker group BlueNoroff - a branch of the notorious Lazarus cybercrime group, through two sophisticated targeted attack campaigns GhostCall and GhostHire.
These campaigns targeted Web3 and cryptocurrency organizations in India, Türkiye, Australia, and several countries in Europe and Asia, and have been ongoing since at least April 2025.
The GhostCall and GhostHire campaigns are said to use new intrusion techniques and custom-designed malware, aiming to infiltrate developer systems and attack blockchain organizations and businesses for financial gain.
These attacks primarily targeted macOS and Windows operating systems and were coordinated through a unified command-and-control infrastructure.
The GhostCall campaign focuses on macOS devices. Attackers approach victims via Telegram, impersonating venture capitalists, and even use compromised accounts of real entrepreneurs and startup founders to propose investment or partnership opportunities.
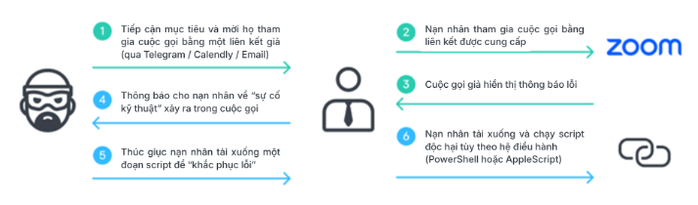
GhostCall Campaign Attack Methodology
Victims are then invited to an “investment meeting” on scam pages that mimic the Zoom or Microsoft Teams interface.
During this fake meeting, the victim will be asked to update the app to fix the audio issue. Once done, the device will download a piece of malicious code and deploy spyware onto the device.
In the GhostHire campaign, this advanced persistent threat (APT) group targeted blockchain developers by impersonating recruiters. Victims were tricked into downloading and running a malicious GitHub repository disguised as a skills test.
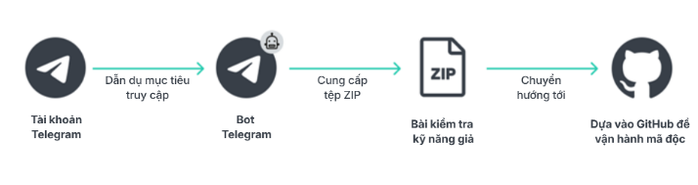
How the GhostHire campaign was attacked
When the victim opens and runs the content, the malware installs itself on the machine, customized to suit the victim's operating system.
Kaspersky recommends being cautious with attractive offers or investment proposals. Always verify the identity of any new contacts, especially if they reach out via Telegram, LinkedIn or other social media platforms.
Be sure to only use authenticated and secure internal communication channels for communications containing sensitive information, always consider the possibility that an acquaintance's account has been compromised, and avoid running unverified scripts or commands just to "fix a bug"...
Source: https://nld.com.vn/chieu-lua-dau-tu-tinh-vi-den-muc-ai-cung-co-the-sap-bay-196251209162029124.htm





![[Photo] Urgently help people soon have a place to live and stabilize their lives](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F1200x675%2Fvietnam%2Fresource%2FIMAGE%2F2025%2F12%2F09%2F1765248230297_c-jpg.webp&w=3840&q=75)









































































![[Photo] General Secretary To Lam works with the Standing Committees of the 14th Party Congress Subcommittees](https://vphoto.vietnam.vn/thumb/402x226/vietnam/resource/IMAGE/2025/12/09/1765265023554_image.jpeg)


































Comment (0)