The scam begins with fake emails impersonating "New Voice Notifications," which look like they come from a legitimate voicemail service.
This email has a "Listen to voicemail" button, which, when clicked, leads the victim through several intermediary websites, including a fake CAPTCHA page to create a sense of security, before redirecting to a complete copy of the Gmail login page.
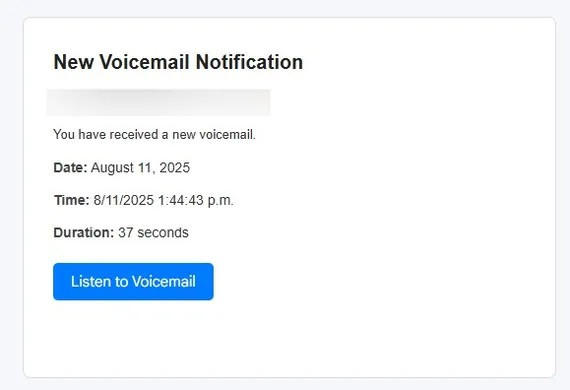
Phishing emails use "new voicemail" notifications to trick users into logging in. (Image: SCS)
Here, users are tricked into entering their email address, password, and even additional security layers such as two-factor authentication codes, backup codes, and security questions. All data is immediately sent to a server controlled by the attacker.
What made this campaign particularly dangerous was that the attackers used the Microsoft Dynamics platform (mkt.dynamics.com), a legitimate marketing service, to host the initial phase.
This method makes it difficult for emails to be flagged as suspicious. The malware creates fake login pages using AES encryption to conceal its identity, features anti-debugging capabilities, and redirects through multiple servers in Russia and Pakistan to hinder investigation.
Experts warn that this represents a major advancement in phishing techniques, combining social engineering (building trust with CAPTCHA and Google interfaces) with exploiting legitimate infrastructure to circumvent censorship.

Gmail passwords can be easily stolen through various scams.
In other news, PCWorld reports that users of Google services, such as Gmail and Google Cloud, are facing a significant increase in phishing attempts.
A Reddit post indicates that Gmail users are currently being targeted by phishing attacks via text messages from phone numbers with the 650 area code.
Scammers posing as Google employees contact victims to warn them about a security vulnerability affecting their accounts. During these calls, the attackers attempt to hijack the victim's Gmail account by asking them to reset their password and provide this information.
Additionally, another phishing technique known as "dangling bucket" has been reported, in which hackers experiment with outdated access addresses to install malware on Google Cloud accounts or steal data.
With 2.5 billion Gmail and Google Cloud users, both businesses and individuals need to be more vigilant against the increasing number of phishing attempts and online attacks.
What should the user do?
- - Always be wary of strange voicemail notifications.
- - Only log in to Gmail through the official Google website.
- - If you suspect you've entered information on a fake website, immediately change your password, check recent login activity, and re-enable security layers.
- Organizations should implement advanced email filtering solutions and train employees on new forms of phishing.
Security teams are also advised to block domains associated with this campaign, particularly horkyrown[.]com, which has been identified as part of the attack infrastructure.
Source: https://khoahocdoisong.vn/nguoi-dung-gmail-doi-mat-chien-dich-lua-dao-chua-tung-co-post2149046980.html


































































































Comment (0)