Release of LockBit 3.0 ransomware analysis report.
Between March 24th and the first week of April this year, Vietnam's cyberspace witnessed a series of targeted ransomware attacks targeting large Vietnamese businesses operating in critical sectors such as finance, securities, energy, and telecommunications. These attacks caused system disruptions for a period of time, resulting in significant economic losses and damage to the reputation of the targeted entities.
Through the process of analyzing and investigating the causes and groups that have recently attacked the information systems of Vietnamese businesses, authorities have found that these incidents are the "products" of various attack groups such as LockBit, BlackCat, Mallox, etc. In particular, regarding the ransomware attack on VNDIRECT's system at 10:00 AM on March 24th, which encrypted all the data of a company ranked among the top 3 on the Vietnamese stock market, authorities have identified LockBit and its LockBit 3.0 malware as the perpetrators.
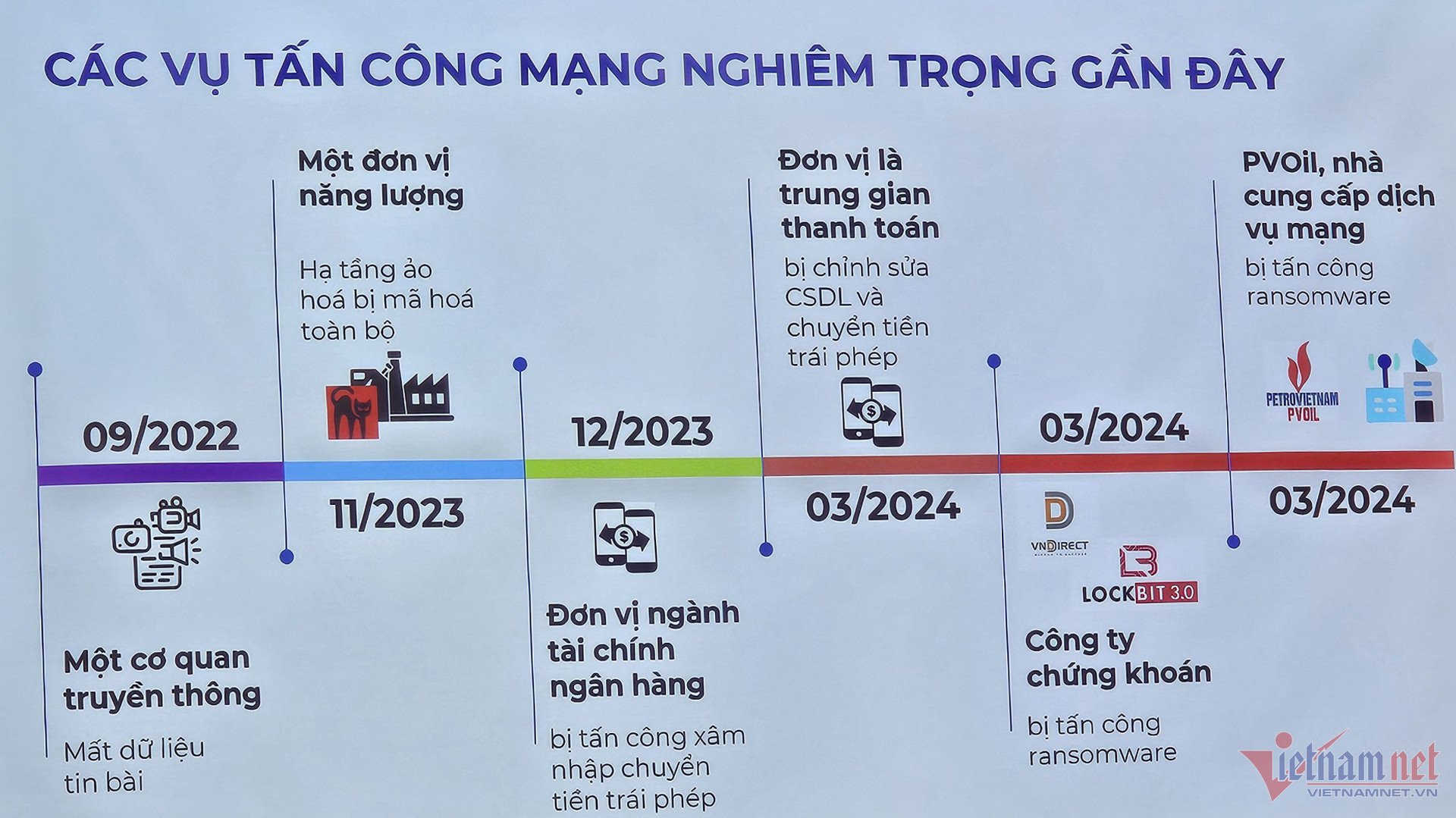
Globally , the LockBit group has launched numerous ransomware attacks targeting large businesses and organizations. For example, in June and October of 2023, this notorious ransomware group attacked the semiconductor manufacturer TSMC (Taiwan, China) and the IT products and services company CDW, demanding ransoms of up to $70-80 million from these businesses.
With the aim of helping agencies, organizations, and businesses in Vietnam better understand the level of danger and how to prevent and mitigate risks from ransomware attacks in general, as well as attacks by the LockBit group in particular, the National Cybersecurity Monitoring Center - NCSC under the Department of Information Security (Ministry of Information and Communications) has compiled information from online sources and released the 'Analysis Report on LockBit 3.0 Ransomware'.
The world's most dangerous ransomware group.
The new report by the NCSC focuses on four main points, including: Information about the LockBit ransomware attack group; Active LockBit clusters; A list of recorded LockBit 3.0-related cyberattack indicators; and Methods for preventing and mitigating risks from ransomware attacks.
Identifying LockBit as one of the world's leading ransomware groups, the NCSC report also stated that since its initial appearance in 2019, LockBit has carried out numerous attacks targeting businesses and organizations across various sectors. The group operates on a 'Ransomware-as-a-Service (RaaS)' model, allowing threat actors to deploy ransomware and share profits with those behind the service.

Notably, in September 2022, the source code of LockBit 3.0, including several names that could be used to develop this ransomware, was leaked by an individual named 'ali_qushji' on the X platform (formerly Twitter). This leak allowed experts to analyze the LockBit 3.0 ransomware more closely, but since then, threat actors have created a wave of new ransomware variants based on the LockBit 3.0 source code.
Along with analyzing the attack methods of active LockBit ransomware clusters such as TronBit, CriptomanGizmo, and Tina Turnet, the NCSC report also provides relevant agencies with a list of recorded IOC (Intelligent Operational Crime) attack indicators related to LockBit 3.0. “We will continuously update IOC indicators on the alert.khonggianmang.vn page of the national cybersecurity portal,” an NCSC expert stated.
A particularly important section of the 'LockBit 3.0 Ransomware Analysis Report' is the guidance provided to agencies, organizations, and businesses on how to prevent and mitigate risks from ransomware attacks. Important notes to support Vietnamese entities in preventing and responding to ransomware attacks, as outlined by the Cybersecurity Department in the 'Handbook on Measures to Prevent and Mitigate Risks from Ransomware Attacks' released on April 6th, continue to be recommended for implementation by NCSC experts.

According to experts, current ransomware attacks often originate from a security vulnerability within an organization. Attackers infiltrate the system, maintain a presence, expand their reach, control the organization's IT infrastructure, and cripple the system, with the goal of forcing victim organizations to pay a ransom to recover their encrypted data.
Speaking to VietNamNet reporters five days after the attack on the VNDIRECT system, a representative from the Information Security Department, speaking from the perspective of the unit coordinating the incident response, stated: This incident is an important lesson to raise awareness of cybersecurity among organizations and businesses in Vietnam.
Therefore, agencies, organizations, and businesses, especially those operating in critical sectors such as finance, banking, securities, energy, and telecommunications, need to urgently and proactively review and strengthen both their existing security systems and personnel, while also developing incident response plans.
"Organizations need to strictly comply with the regulations, requirements, and guidelines on information security and cybersecurity that have been issued. This is the responsibility of each organization and business to protect itself and its customers from potential cyberattack risks," a representative from the Information Security Department emphasized.
| The LockBit ransomware was first known as ABCD, named after the encrypted file extension, and after a few months, a variant of ABCD appeared under its current name, Lockbit. A year later, the group released an upgraded version, LockBit 2.0 (also known as LockBit Red), which included another integrated malware called StealBit, aimed at stealing sensitive data. LockBit 3.0, or LockBit Black, is the latest version, released in 2022, with new features and advanced security circumvention techniques. |

Why was the PVOIL system able to recover so quickly after a ransomware attack?

Develop a security culture to enhance defenses against ransomware attacks.

Paying ransom for data will encourage hackers to increase ransomware attacks.
Source




![[Photo] Prime Minister Pham Minh Chinh presides over a meeting on private sector economic development.](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F1200x675%2Fvietnam%2Fresource%2FIMAGE%2F2025%2F12%2F20%2F1766237501876_thiet-ke-chua-co-ten-40-png.webp&w=3840&q=75)





































































































Comment (0)