In today’s digital age, cyber attacks are becoming more sophisticated and dangerous than ever. Recently, a complex cyber attack was discovered targeting computers in Ukraine, with the goal of deploying Cobalt Strike malware and taking control of infected servers. This attack not only utilized advanced techniques to penetrate the system, but also used a variety of evasive measures to avoid detection by security software. In this article, we will take a detailed look at how the attack took place, the techniques used by the hackers, and simple measures you can take to protect yourself from similar threats.
Part 1: Sophisticated Hacker Attack Techniques
Now that we understand the context and importance of uncovering this sophisticated cyber attack, let's dive into the details to see how the hackers carried out this attack.

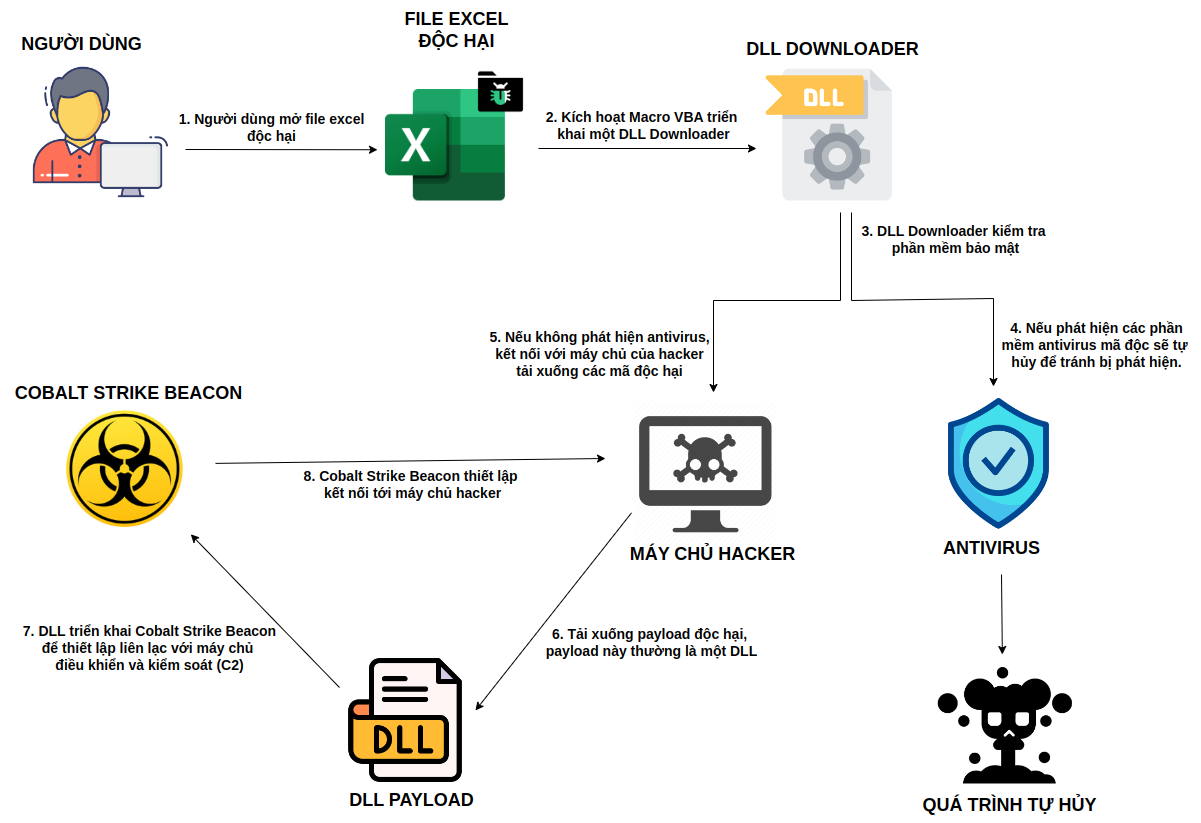
The attack takes place in a basic 8-step process as follows:
Step 1: User opens malicious Excel file
Hackers send a malicious Excel file to victims via email or other means. When users open the file, they are prompted to enable content to enable macros.
Step 2: Enable VBA Macro to Deploy a DLL Downloader
When the user enables the macro, the VBA code embedded in the Excel file starts executing and deploys a DLL Downloader using the register server system utility (regsvr32).
Step 3: DLL Downloader checks for security software
DLL Downloader checks if security software like Avast Antivirus or Process Hacker is running on the system.
Step 4: If antivirus software is detected, the malware will self-destruct to avoid detection.
If security software is detected, the malware will self-destruct to avoid detection and containment.
Step 5: If no antivirus is detected, connect to the hacker's server and download the malicious code
If no security software is detected, DLL Downloader will connect to the hacker's command and control (C2) server to download the next stage encryption payload.
Step 6: Download the malicious payload, which is usually a DLL
The next stage encryption payload is downloaded and is usually a DLL file. This file is responsible for launching the next step in the attack chain.
Step 7: DLL deploys Cobalt Strike Beacon to establish communication with the command and control (C2) server
The downloaded DLL file will deploy Cobalt Strike Beacon, a special payload used to establish communication with the hacker's C2 server.
Step 8: Cobalt Strike Beacon establishes connection to hacker server
Cobalt Strike Beacon establishes communication with a C2 server, allowing hackers to take full control of the infected computer and conduct malicious activities such as data theft, remote control, and surveillance.
Part 2: Hackers' sophisticated evasion techniques
Now that we understand how the attack works, we need to know more about how the hacker avoids detection to be successful in this attack.
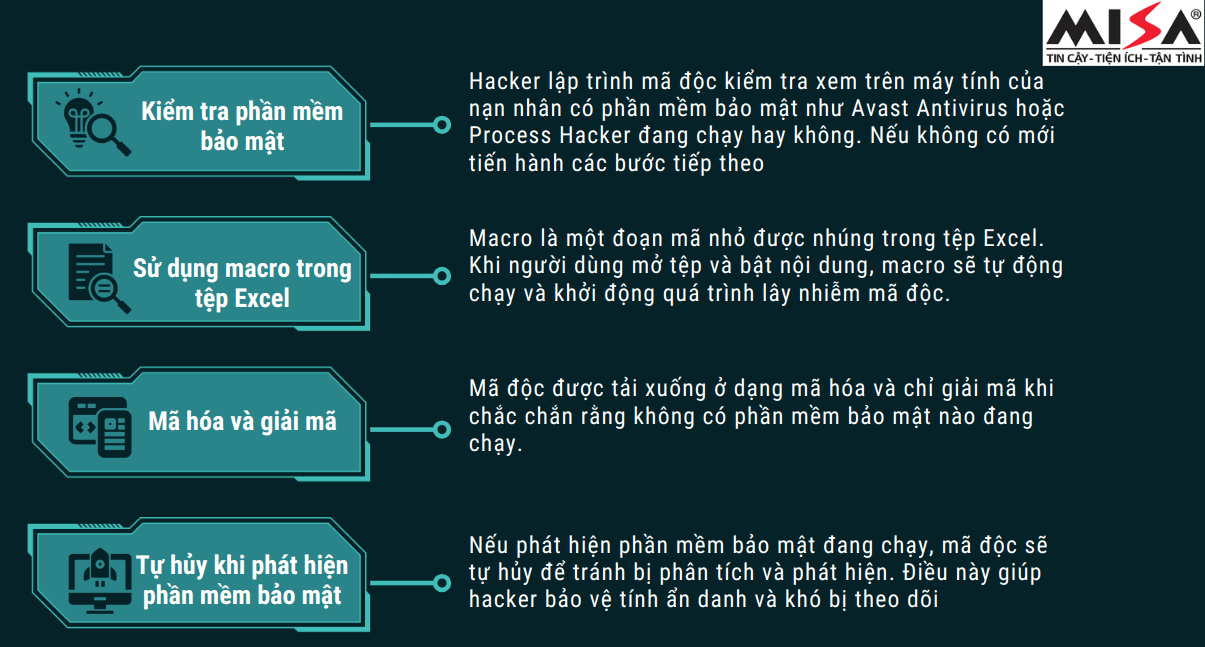
Hackers use sophisticated evasion techniques to ensure their attacks are successful without being detected. Understanding these techniques helps us better understand the dangers of today's cyber attacks and, in turn, apply appropriate protection measures.
Part 3: Best Protection Measures for Users
With the rise of sophisticated cyber attacks, protecting your systems and data is more important than ever. Here are some top tips to help you effectively enhance your cyber security:
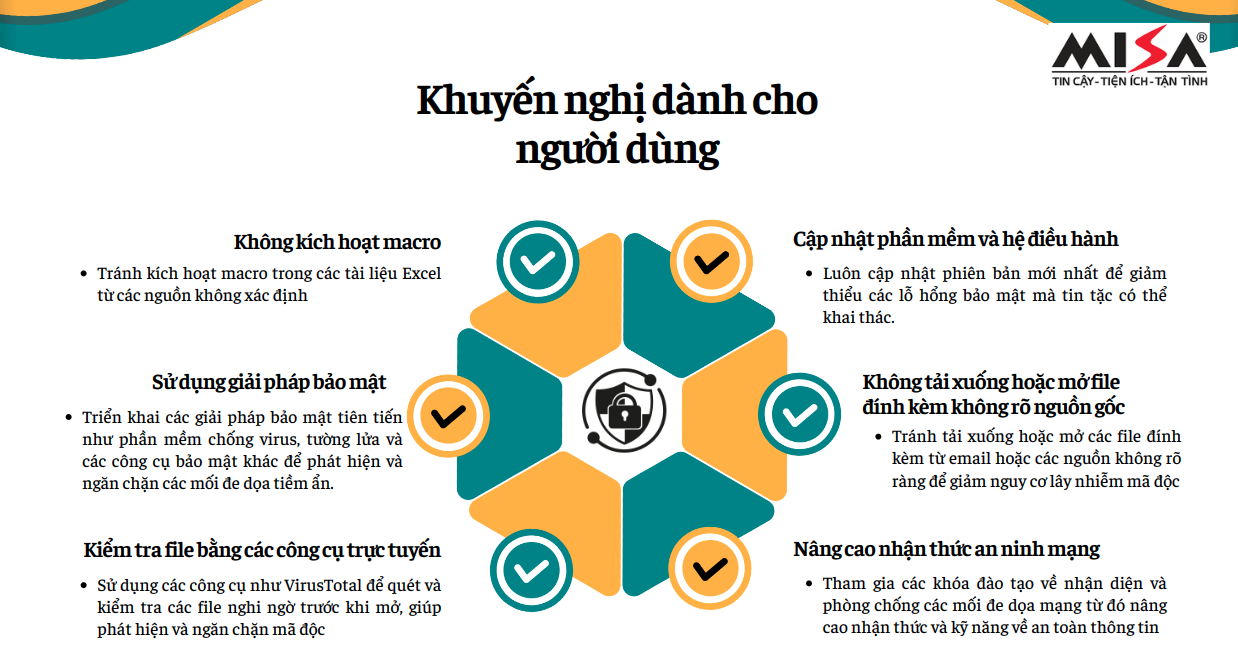
With the rise of sophisticated cyberattacks, it is important to protect your systems and personal data. By not enabling macros from untrusted sources, keeping your software up to date, using robust security solutions, and checking files with tools like VirusTotal, you can minimize the risk of malware infection. Stay vigilant and follow security measures to protect yourself against cyberthreats.
Source: https://www.misa.vn/147305/canh-bao-excel-macro-tinh-nang-cu-ky-thuat-tan-cong-moi/






![[INFOGRAPHIC] Open-back headphones, look like a... pill](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/7/16/cd63f007ad404018aa504c1009ce19ba)




























































































Comment (0)