With Apple's iOS operating system built on closed source code, the iPhone is often considered more secure than some other phones when it comes to protecting personal data.
However, no system is completely secure and it is entirely possible for cybercriminals to exploit vulnerabilities in the iPhone's operating system to carry out attacks that steal user data.
If you have any doubts about the security and privacy of your iPhone, it is important to check it right away.

How to know if your iPhone is hacked
When your iPhone is hacked, all of your personal information, from messages, photos, videos , and even your current location, can be accessed and tracked by bad guys. Therefore, knowing how to recognize a hacked iPhone will help you quickly identify the situation and find the fastest solution.
iPhone battery drains fast
The iPhone battery can run out quickly for two reasons: One is that your iPhone's battery capacity has decreased, and the other is that your iPhone has been hacked. In the first case, the iPhone battery has been used for many years, so it has worn out over time.
However, if the battery has been used for a short time and the wear and tear has occurred, it is very likely that your iPhone has been hacked by a bad guy. Background running applications or personal information being stolen or compromised are the reasons behind the iPhone's quick battery drain.
Unusual network data usage
If you use your 3G or 4G network data, it will cost more than normal when your iPhone is hacked because there are many applications accessing your network data at the same time.
This is a concern because your personal information and data will be revealed when third-party software appears running in the background on your iPhone.

When your iPhone is hacked, all of your personal information from messages, photos, videos, and even your current location can be accessed and tracked by bad guys.
Frequent loss of signal
Interference will occur when the iPhone is hacked, especially when making phone calls. In addition, when other strange noises appear such as clicking, echoing, accompanied by interference, you must be completely alert. Because important information in the call may be being eavesdropped by others.
Strange application message appears
When your iPhone shows unusual signs such as strange messages, strange applications are displayed frequently on the notification bar, that is also a way to identify that the iPhone has been hacked. The purpose of these spam messages and strange links is to attract the attention and curiosity of users, thereby leading to websites that have pre-installed tools to steal personal accounts.
How to handle when iPhone is hacked
Disconnect from the internet
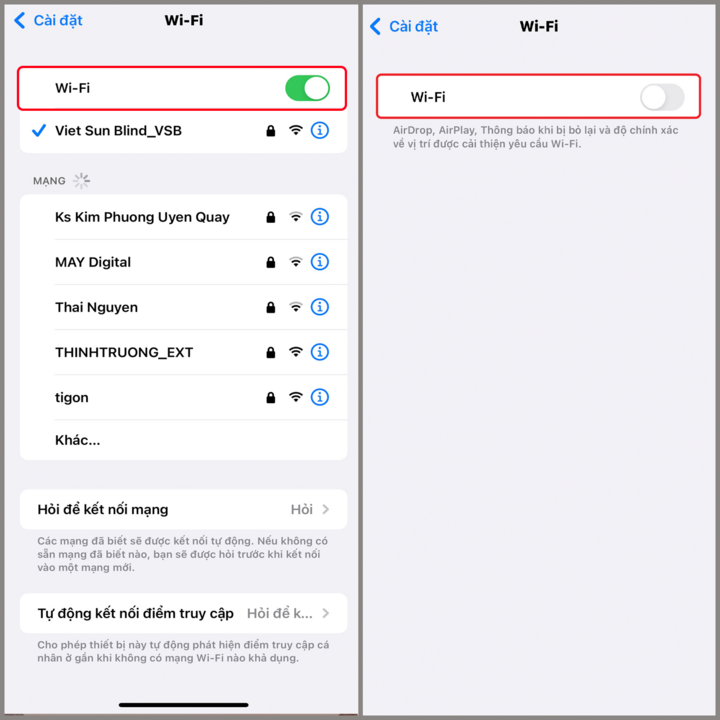
Disconnecting the Internet, switching the iPhone to airplane mode and removing the SIM card are ways to defend against being hacked by bad guys. Do the following: Go to Settings > Select Wifi > Disconnect Wifi.
You can also do the same to disconnect from the mobile network as follows: Go to Settings > Mobile network (3G/4G) > Disconnect network .
Restore factory settings
Installation errors are also the reason why hackers can easily break into your data. To restore the factory settings, you need to follow these steps:
Go to Settings > Select General settings > Select Transfer or Reset iPhone > Select Reset > Select Reset all settings .
Check battery usage
Malware present in hacked iPhones will consume more power, causing the battery to drain faster and leading to many other battery-related problems.
You can check the battery usage on your iPhone by doing the following: Select Settings > Battery .
Normally, iPhone will notify users of battery usage in the last 24 hours and in the last 10 days. Therefore, do a check now to see which apps running in the background are consuming battery and remove them immediately.
Check Ram, CPU usage
Strange applications that have high RAM and CPU usage will cause the iPhone to heat up and reduce performance. Some applications you can use to check CPU and RAM usage are Battery Pro, AIDA64, Camera, Netwwork.
Specifically, if the usage capacity has exceeded the limit, delete unnecessary memory-consuming applications from the device. If it is still within the allowed limit, you can perform operations to help reduce the iPhone temperature such as reducing screen brightness or turning off the application refresh feature.

Remove untrusted apps
You need to remove untrusted applications from your device to avoid iPhone hacking by following these steps:
Step 1: Go to Settings > Select General Settings > Select iPhone Storage .
Step 2: Select the application to delete > Select Delete application .
Step 3: Select Delete App .
Tra Khanh
Source









![[Infographic] Phong Nha-Ke Bang National Park and Hin Nam No National Park - The first transboundary world heritage of Vietnam and Laos](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/7/14/e6edaedb8e7345e484b074affac0739b)






















































































Comment (0)