The method, called TSforge Activation, allows hackers to permanently activate most Microsoft products while completely bypassing the company's digital rights management (DRM) system.
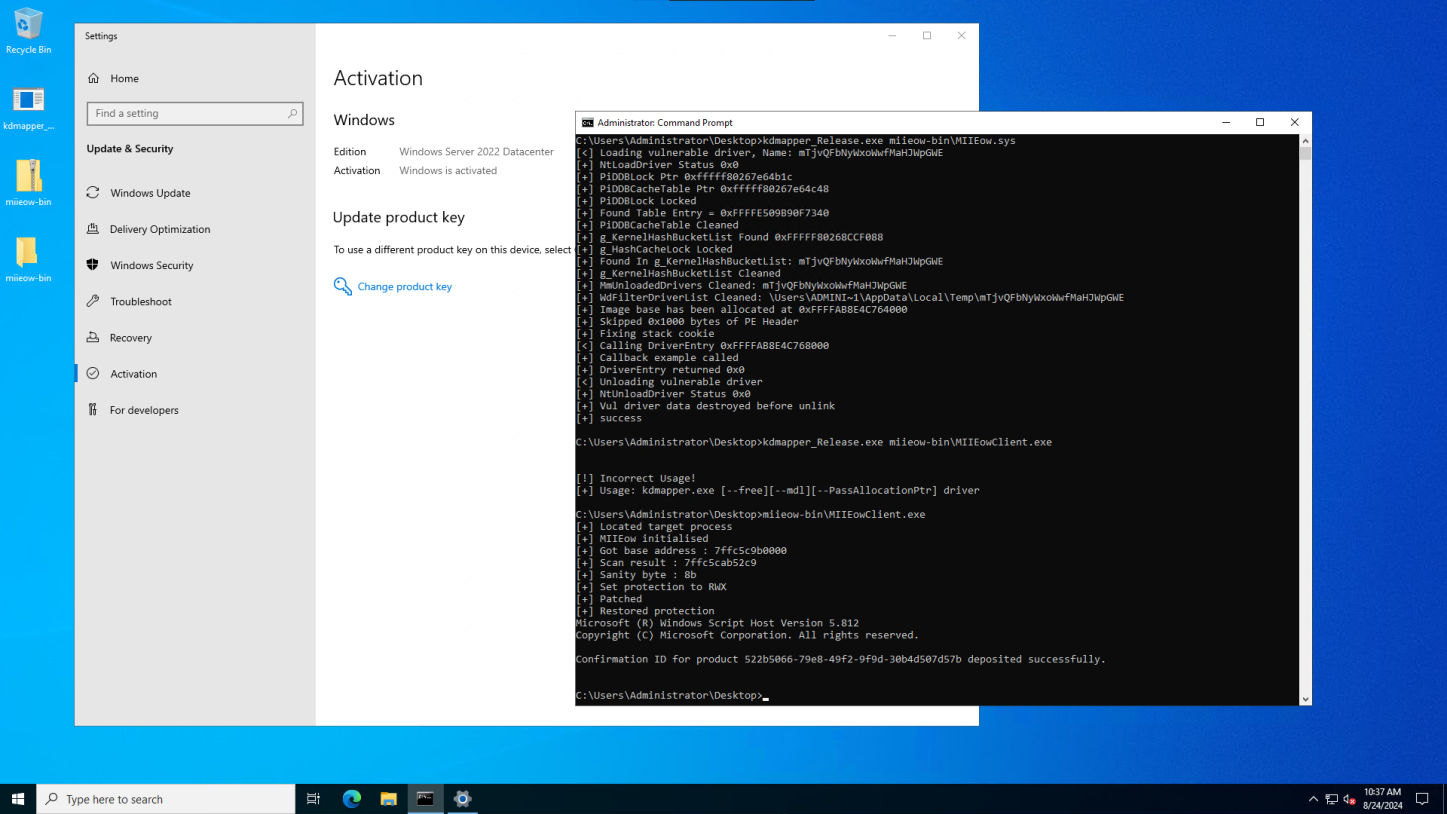
TSforge Activation is integrated into Massgrave's MAS 3.0 tool
In 2024, the hacker group introduced a project called Microsoft Activation Scripts (MAS). In the latest MAS 3.0 update, Massgrave added the TSforge Activation method, along with patches and improvements to existing activation scripts. The group claims that TSforge is one of the most powerful and extensive exploits ever added to MAS.
How MAS bypasses Microsoft's protection system
In a recent blog post, Massgrave shared details about how they discovered and developed this hack, and explained how they bypassed Microsoft's activation protection system, called Software Protection Platform (SPP). The SPP system is described as "extremely complex," with product activation information stored in two main files, "data.dat" and "tokens.dat."
While Massgrave touts SPP as an advanced DRM system, it can still be circumvented. The TSforge method works by injecting fake data into these repositories, bypassing any checks and causing SPP to recognize the fake product key or confirmation ID as valid.
The TSforge activation method supports multiple versions of Windows, from Windows 7 to Windows Server 2025, as well as Office 2013 to 2024. Users can activate add-ons for commercial Windows licenses, including the Extended Security Updates (ESU) program for some versions of Windows 7 to 10.
The MAS toolkit is an open source project hosted on GitHub, which is owned by Microsoft, so the team maintains that they are not involved in copyright infringement. The group describes their activation method as an alternative that they say Microsoft support staff can use when other methods fail.
Microsoft has not yet made any official response to this information.
Source: https://thanhnien.vn/xuat-hien-cong-cu-co-the-kich-hoat-phan-mem-cua-microsoft-185250225135610115.htm



![[Photo] Da Nang residents "hunt for photos" of big waves at the mouth of the Han River](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/10/21/1761043632309_ndo_br_11-jpg.webp)
![[Photo] Prime Minister Pham Minh Chinh received Mr. Yamamoto Ichita, Governor of Gunma Province (Japan)](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/10/21/1761032833411_dsc-8867-jpg.webp)
![[Photo] Prime Minister Pham Minh Chinh meets with Speaker of the Hungarian National Assembly Kover Laszlo](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/10/20/1760970413415_dsc-8111-jpg.webp)







































































































Comment (0)