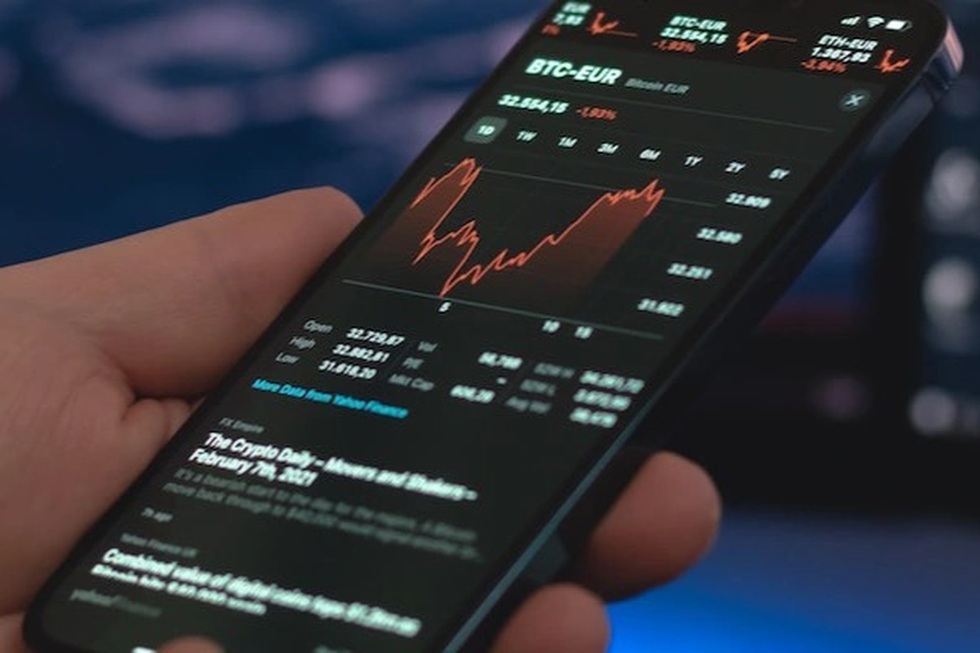
Scammers can plan scams and exploit technology to take advantage of users' trust. Many people who invest in cryptocurrencies have fallen victim to these schemes.
Advanced phishing attacks
Phishing attacks targeting crypto wallets and exchange accounts can be carried out through various sophisticated tactics, exploiting user trust to steal private keys or login credentials.
To carry out these attacks, attackers create fake websites that look like legitimate platforms. They then send phishing emails impersonating trusted organizations to trick victims into sharing sensitive information.

Criminals can create fake websites that look similar to legitimate platforms (Photo: National Economy Newspaper).
The attacker may employ the following sophisticated tactics:
- Wallet drainers: These are malicious programs used in phishing attacks. After a victim connects their wallet to a fraudulent website and approves a malicious transaction or grants token authorization, the attacker can automatically transfer funds out of the wallet.
- Quishing (QR Code Scams): Scammers use malicious QR codes placed in emails, text messages, or public places. When scanned, these codes redirect users to phishing websites or trigger malicious downloads to steal personal, financial, or authentication information.
- Spear phishing: This method targets specific individuals or organizations. Scammers craft personalized messages, often using urgent phrases like "Immediate action required" to create panic and pressure victims into making mistakes.
Last August, a developer's cryptocurrency wallet on the Ethereum network was emptied after he installed a malicious extension. After his private key was stolen, all of his cryptocurrency was transferred away.
Rug pull (Liquidation withdrawal)
Scammers often exploit decentralized finance (DeFi) platforms and NFT projects to do this. Rug pull is a common tactic, where developers suddenly withdraw liquidity and disappear with investors' funds.
These projects often promise unusually high returns or exclusive digital assets. Many are hyped up excessively on social media but offer no real value.
Rug pull is a common tactic where developers suddenly withdraw liquidity and disappear with investors' money (Photo: CNN).
Warning signs of a rug pull scheme include unrealistic promises of high returns with low risk, anonymous teams unwilling to share their identities, or a lack of transparent auditing.
According to CoinTelegraph , since the beginning of 2025, rug pulls have caused nearly $6 billion in losses within the Web3 ecosystem. A prominent example is the Libra token on the Solana network. The token's market value skyrocketed after being mentioned by the President of Argentina on social media platform X. After the post was deleted, the token's price dropped by more than 94%, leading to allegations of a rug pull.
Impersonation
Impersonation is a common problem on social media. Scammers will impersonate trusted influencers, developers, or support staff on platforms like X.
They then infiltrate conversations or create fake profiles to exploit users seeking quick profits. Scammers often organize fake giveaway programs, promising double returns for sending a small "verification" fee.
They may also create fake accounts impersonating celebrities or send direct messages posing as exchange support staff to gain access to wallets or request urgent fund transfers.
In 2024, crypto scams caused $9.9 billion in losses globally, with impersonation scams increasing fourfold.
Deepfake scams are powered by AI.
AI-powered deepfake scams have emerged as a major threat, using advanced technology to deceive users and steal assets. Criminals leverage artificial intelligence (AI) to create incredibly realistic videos or voiceovers of executives, influencers, and celebrities.

Deepfake scams using AI have emerged as a major threat (Photo: GlobalNews).
These deepfake contents are highly misleading and can deceive even cautious users. They blur the lines between real and fake communication, exploit trust, and create a fear of missing out (FOMO).
In August 2024, the New York Times called Elon Musk's deepfake version "the biggest scam on the internet." Steve Beauchamp (82 years old) was convinced by the deepfake video and invested his entire savings of $690,000 over several weeks. The money then disappeared.
Fake Crypto Support
Scams involving fake crypto support are a growing threat. Fraudsters often impersonate customer support staff from trusted exchanges or wallet providers.
They will contact victims through social media platforms like X, Telegram, or fake websites that closely resemble the official domain. By offering seemingly genuine support, they will exploit the user's trust.
Some common tactics used include sharing phishing links disguised as support portals, requesting private keys or security phrases (seed phrases), etc.
Source: https://dantri.com.vn/cong-nghe/5-chieu-tro-lua-dao-tien-dien-tu-pho-bien-20251008005941088.htm







![[Photo] General Secretary To Lam receives President of the European Council Antonio Costa](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F1200x675%2Fvietnam%2Fresource%2FIMAGE%2F2026%2F01%2F29%2F1769697816651_a1-bnd-5216-9741-jpg.webp&w=3840&q=75)





















































































![OCOP during Tet season: [Part 3] Ultra-thin rice paper takes off.](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F402x226%2Fvietnam%2Fresource%2FIMAGE%2F2026%2F01%2F28%2F1769562783429_004-194121_651-081010.jpeg&w=3840&q=75)


![OCOP during Tet season: [Part 2] Hoa Thanh incense village glows red.](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F402x226%2Fvietnam%2Fresource%2FIMAGE%2F2026%2F01%2F27%2F1769480573807_505139049_683408031333867_2820052735775418136_n-180643_808-092229.jpeg&w=3840&q=75)
![OCOP during Tet season: [Part 1] Ba Den custard apples in their 'golden season'](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F402x226%2Fvietnam%2Fresource%2FIMAGE%2F2026%2F01%2F26%2F1769417540049_03-174213_554-154843.jpeg&w=3840&q=75)





Comment (0)