
Part 1: Phishing Campaign Using Cloudflare Workers
Cybersecurity researchers have warned of several phishing campaigns that are leveraging Cloudflare Workers to harvest user login credentials. These phishing sites target users of services like Microsoft, Gmail, Yahoo!, and cPanel Webmail.
Here, the attacker used a technique called “ Adversary-in-the- Middle” (AitM). To carry out the attack, the attacker used Cloudflare Workers as a fake intermediary server. When a user visits a legitimate login page, Cloudflare Workers intercepts and forwards data between the user and the real login page.
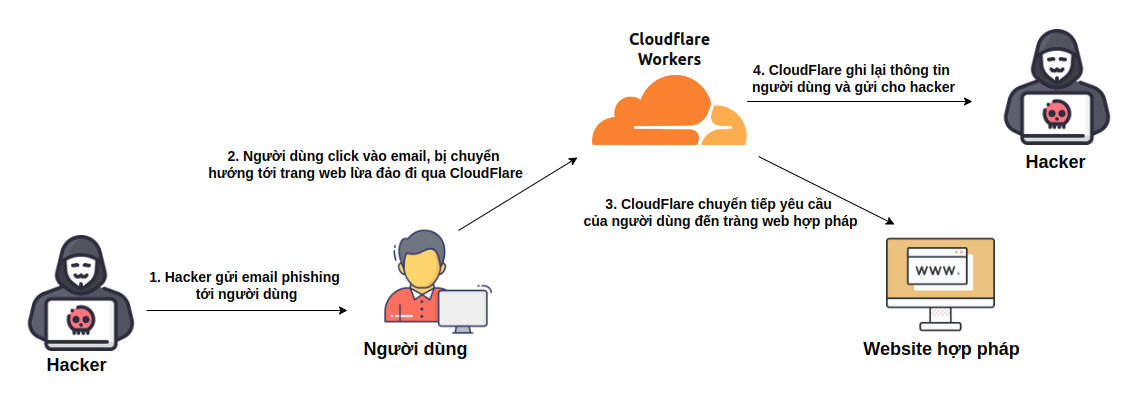
Basically, this attack will take place through the following 4 steps:
- Step 1: Hacker sends phishing email to user
An attacker sends a phishing email containing a link to a fake website. The email may appear to come from a trusted source and contain a message that persuades the user to click the link.
- Step 2: User clicks on email, redirected to phishing website via Cloudflare
The user receives the email and clicks on a link in the email, which takes them to a fake website. The website is hosted on Cloudflare Workers, so the user's request goes through Cloudflare Workers.
- Step 3: Cloudflare forwards the user's request to the legitimate website
When a user enters their login information into the fake site, Cloudflare Workers captures the login information (including username, password, and two-factor authentication code if available). Cloudflare Workers then forwards the request to the legitimate site. The user remains logged into the legitimate site without noticing any difference.
- Step 4: Cloudflare records user information and sends it to hackers
Cloudflare Workers capture the user's login information and send it to the attacker. The attacker can then use this information to access the user's account and perform malicious actions.
Part 2: HTML Smuggling Techniques and Credential Harvesting Strategies
HTML Smuggling is a sophisticated attack method that attackers use to stealthily create fraudulent pages right on the user's browser.
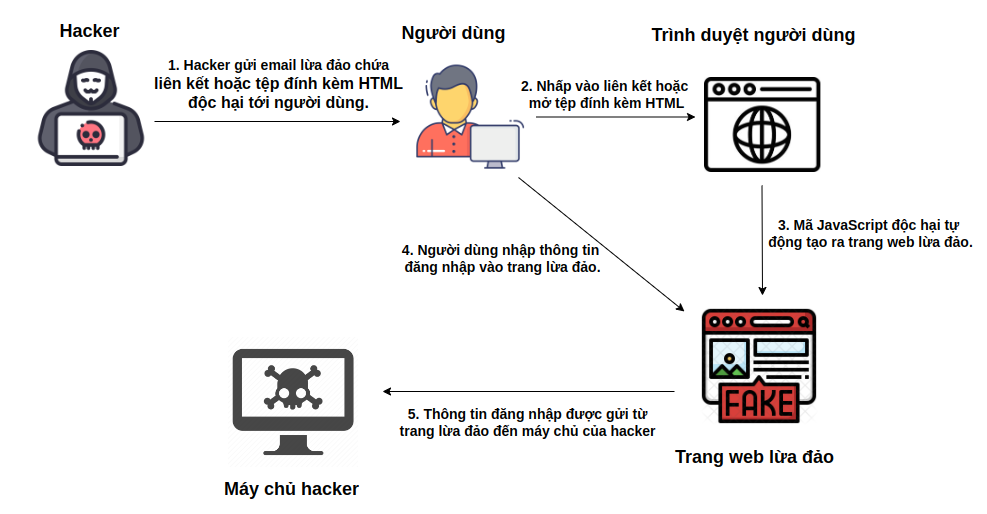
Basically, an HTML Smuggling attack takes place in 5 main steps:
- Step 1: Attacker sends phishing email
The attacker creates a phishing email, pretending to be from a trusted source, such as an organization or service the victim frequently uses. The email contains a link or a malicious HTML attachment. The email body typically includes a convincing or urgent message that entices the victim to open the link or attachment, such as a notification about a locked account or an important document that needs to be viewed immediately.
- Step 2: User receives email and opens link/attachment
A user receives a phishing email and, unsuspecting, clicks on a link or opens an HTML attachment. When they do so, the user's browser loads and executes malicious JavaScript code contained in the HTML file or link. This code is designed to run directly in the user's browser without requiring the download of any additional software.
- Step 3: JavaScript code creates a phishing page right on the user's browser
Malicious JavaScript code automatically generates a phishing page and displays it in the user's browser. This phishing page often looks very similar to the legitimate login page of an online service like Microsoft, Gmail, or any other service the victim commonly uses. This makes the victim not realize that they are on a fake page.
- Step 4: User enters login information into phishing site
Without warning, the user enters their login information into the phishing site. This includes their username, password, and possibly a two-factor authentication (MFA) code if requested. The phishing site is designed to record all of this information in secret.
- Step 5: Login information is sent to the hacker's server
When a user enters their login information on the phishing page, the malicious JavaScript code sends that information back to the hacker’s server. This allows the attacker to collect the victim’s login information, including the username, password, and two-factor authentication code. With this information, the attacker can gain unauthorized access to the victim’s account.
Part 3: User recommendations on precautions
To protect yourself from the increasingly sophisticated cyberattacks mentioned above, users need to take some precautions to minimize the risk. Here are some important recommendations:
- Raising awareness of cyber security
In today's digital environment, cyberattacks are constantly evolving and becoming increasingly sophisticated. Therefore, it is extremely important to stay updated on the latest cyber security threats. Users should actively monitor reputable and updated information sources to understand the risks and know how to prevent them.
- Use Two-Factor Authentication (2FA):
Two-factor authentication adds an extra layer of security. Even if an attacker gets your login information, they'll still need a second authentication code to access your account.
- Always check and verify before taking action
Double check all attachments and links before clicking.
THINK CAREFULLY BEFORE CLICKING!!!
- Use Antivirus software
Antivirus software is capable of scanning and detecting various types of malware such as viruses, trojans, ransomware, spyware, and other threats. When detected, it removes or quarantines the malware to protect your system.
In today’s digital age, cyberattacks are becoming more sophisticated and harder to detect. It is important to understand and guard against phishing campaigns using Cloudflare Workers and HTML Smuggling. To protect yourself, users should regularly update their cybersecurity knowledge, use a password manager, install antivirus software, and implement two-factor authentication. These measures not only help protect personal information but also contribute to improving cybersecurity for the entire community.
— General Security Department —
Source: https://www.misa.vn/147167/giai-ma-cac-chien-thuat-tan-cong-phishing-hien-dai-tu-cloudflare-workers-den-html-smuggling/




















































![[Maritime News] More than 80% of global container shipping capacity is in the hands of MSC and major shipping alliances](https://vphoto.vietnam.vn/thumb/402x226/vietnam/resource/IMAGE/2025/7/16/6b4d586c984b4cbf8c5680352b9eaeb0)










































Comment (0)