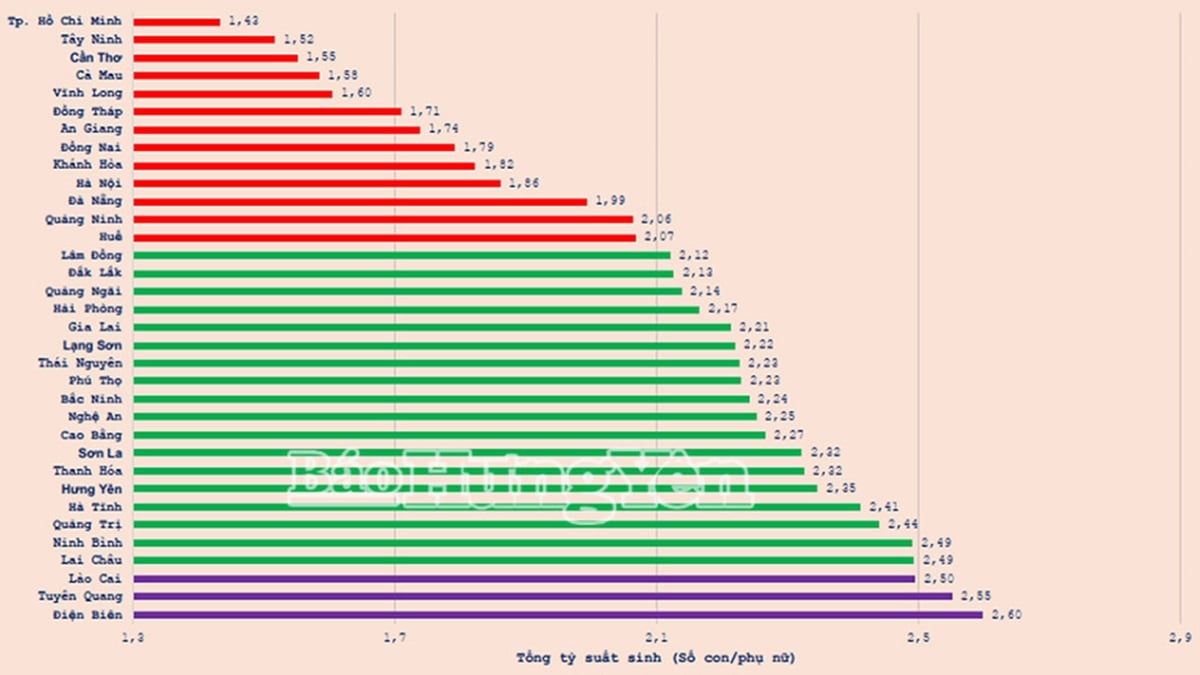
 |
A flaw in a train that could be exploited to control the train's brakes. Photo: AAR . |
The US Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning about a critical train system that can be hacked with just a radio and a little technical knowledge. The vulnerability lies in the protocols used in the train system called “End-of-Train” and “Head-of-Train”.
A device mounted at the end of the train, called the FRED (Flashing Rear End Device), transmits data via radio waves to a corresponding device at the front of the train. Commands can also be sent from the front of the train to the FRED to activate the brakes at the end of the train.
These devices were first installed in the 1980s to replace end cars, but they do not have any encryption or authentication mechanisms. The current system relies on transmitting data packets between the front and back of the train, with a simple checksum (BCH checksum) to detect errors or interference.
However, CISA warns that with just a software-controlled radio device, an attacker could send out spoofed signals to interfere with train operations. “If successfully exploited, an attacker could send a brake command to a device at the end of the train, causing the train to stop abruptly, disrupting its schedule or even damaging the braking system,” the agency said.
The vulnerability was reported to the agency by two researchers, Neil Smith and Eric Reuter. Smith wrote on X that he had alerted the Industrial Control Systems Cybersecurity Emergency Response Team (ICS-CERT), which is managed by CISA, about the risk in 2012 but that no action had been taken to fix the issue at the time.
“You can remotely control the braking system of a train from a great distance, with equipment that costs less than $500 ,” Smith wrote on X. He warned of the risk that could lead to train derailments, or even the paralysis of the entire national rail system.
According to Smith, from 2012 to 2016, he faced difficulties from the Association of American Railroads (AAR), which considered the risk theoretical and required real-world evidence that an attack could happen before considering action.
In 2024, Smith raised the issue with the agency again and received a similar response. But in April, the organization finally announced that it would begin upgrading the outdated system starting in 2026.
CISA's Deputy Executive Director for Cybersecurity, Chris Butera, downplayed the current risk associated with the terminal vulnerability in a statement to Gizmodo . He said the vulnerability has been known and monitored by rail industry stakeholders for more than a decade.
“To exploit this vulnerability, an attacker would need physical access to the railway, in-depth knowledge of the technical protocol, and specialized equipment,” Butera said. These requirements are difficult to meet, making large-scale attacks less likely.
Butera added that CISA is working with industry partners to develop mitigation measures and confirmed that a fix is in the works.
Source: https://znews.vn/hacker-co-the-dieu-khien-tau-hoa-bang-radio-post1568968.html






























































![[Maritime News] More than 80% of global container shipping capacity is in the hands of MSC and major shipping alliances](https://vphoto.vietnam.vn/thumb/402x226/vietnam/resource/IMAGE/2025/7/16/6b4d586c984b4cbf8c5680352b9eaeb0)


































Comment (0)