
According to data released by Kaspersky Security Network, the number of ransomware detections decreased by 18% from 2023 to 2024, from 5,715,892 to 4,668,229.
However, the percentage of users affected by ransomware attacks increased slightly by 0.44%. This small percentage is directed towards high-value targets, making ransomware even more dangerous.
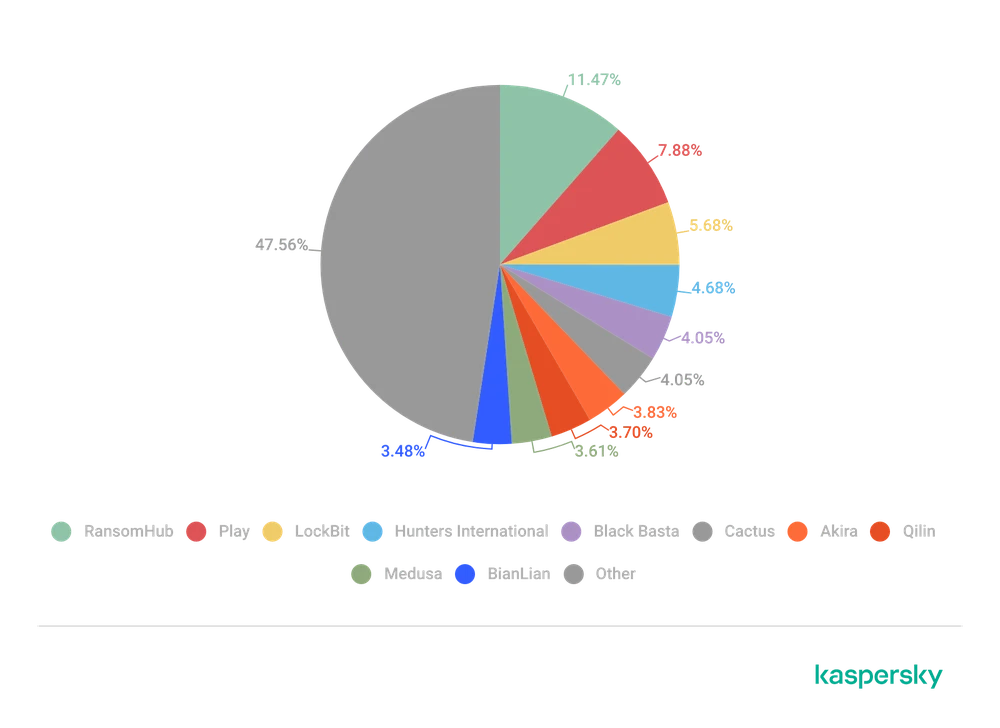
Kaspersky's Global Cybersecurity Response Team (GERT) says that 41.6% of cybersecurity incidents in 2024 will involve ransomware, up from 33.3% in 2023. Targeted ransomware is likely to remain the main threat to organizations worldwide .
At the same time, ransomware source codes are "renovated" with additional tools, even the FunkSec group, which specializes in attacking financial andeducational organizations, also uses AI to further develop the power of ransomware, avoiding detection.
Many ransomware attacks still target Windows-based systems due to its widespread use in corporate environments. Windows' architecture, combined with vulnerabilities in software like the Remote Desktop Protocol (RDP) and unpatched systems, make it a prime target for ransomware executables.
In addition, third-party attacks are drivers that are digitally signed by a trusted organization or Microsoft. In parallel, in recent years, some attack groups such as RansomHub and Akira have diversified their targets to develop Ransomware variants that target Linux and VMware systems, especially in cloud and virtualization environments as organizations adopt cloud and hybrid system setups.
Ransom payments for data breaches dropped significantly in 2024 to around $813.55 million, down 35% from a record $1.25 billion in 2023, according to Chainalysis.
Notably, Sophos reports that the average ransom payment increased from $1,542,333 in 2023 to $3,960,917 in 2024, reflecting a trend of ransomware targeting larger organizations with higher demands.

Some cybercriminal groups not only extort money by encrypting data, they also exploit the sensitive data they have stolen as leverage to extend their threats to third parties such as the victim’s customers, partners, suppliers, etc. They target identified organizations to cause disruption and maximize their payouts, focusing on high-value targets such as hospitals, financial institutions, and government agencies.
Mr. Ngo Tran Vu, NTS Security Company said that enabling the Vulnerable Driver Blocklist function of Windows in the Device Security - Core isolation section is very important to prevent BYOVD attacks. It is very important for Windows users to regularly update Windows patches and patch updates of software installed on their computers. For businesses, it is necessary to regularly scan for vulnerabilities and prioritize high-severity errors, especially in widely used software such as Microsoft Exchange or VMware ESXi, which are increasingly targeted by ransomware.
To effectively combat ransomware in 2025, organizations and individuals must adopt a multi-layered defense strategy to address the evolving tactics of groups like FunkSec, RansomHub, and others leveraging AI, according to Kaspersky. Prioritize proactive prevention through patching and vulnerability management. Many ransomware attacks exploit unpatched systems, so organizations should deploy automated patch management tools to ensure timely updates to operating systems, software, and drivers.
"For small businesses, they can take advantage of the Kaspersky Plus solution in parallel with Windows Security to increase multi-layer protection, prevent malware and prevent exploits as well as better protect data," Mr. Ngo Tran Vu added.
Source: https://www.sggp.org.vn/ransomware-nguy-hiem-hon-o-nam-2025-post794617.html






























































![[Maritime News] More than 80% of global container shipping capacity is in the hands of MSC and major shipping alliances](https://vphoto.vietnam.vn/thumb/402x226/vietnam/resource/IMAGE/2025/7/16/6b4d586c984b4cbf8c5680352b9eaeb0)




































Comment (0)