According to BleepingComputer , Microsoft has added the BioNTdrv.sys driver to its blocked list due to a security vulnerability that could be exploited by hackers. The vulnerability was found in a kernel-level driver within the Paragon Partition Manager software. Hackers could exploit this driver to gain system-level control on Windows, thereby launching ransomware attacks. If the software is already installed on the target device, attackers can exploit the existing vulnerability. Conversely, they could also install this driver to infiltrate the system in their own way.
According to CERT/CC, these vulnerabilities allow hackers to gain local access to the device, potentially escalating privileges or causing denial-of-service (DoS) attacks. Specifically, because the BioNTdrv.sys driver is digitally signed by Microsoft, hackers can employ the "Bring Your Own Vulnerable Driver" (BYOVD) technique, exploiting legitimate but vulnerable drivers to compromise the system.
Microsoft stated that four of the five vulnerabilities affect Paragon Partition Manager versions 7.9.1 and earlier, while the fifth vulnerability (CVE-2025-0298) impacts version 17 and older. This is also a vulnerability that has been actively exploited by hackers in recent ransomware attacks.
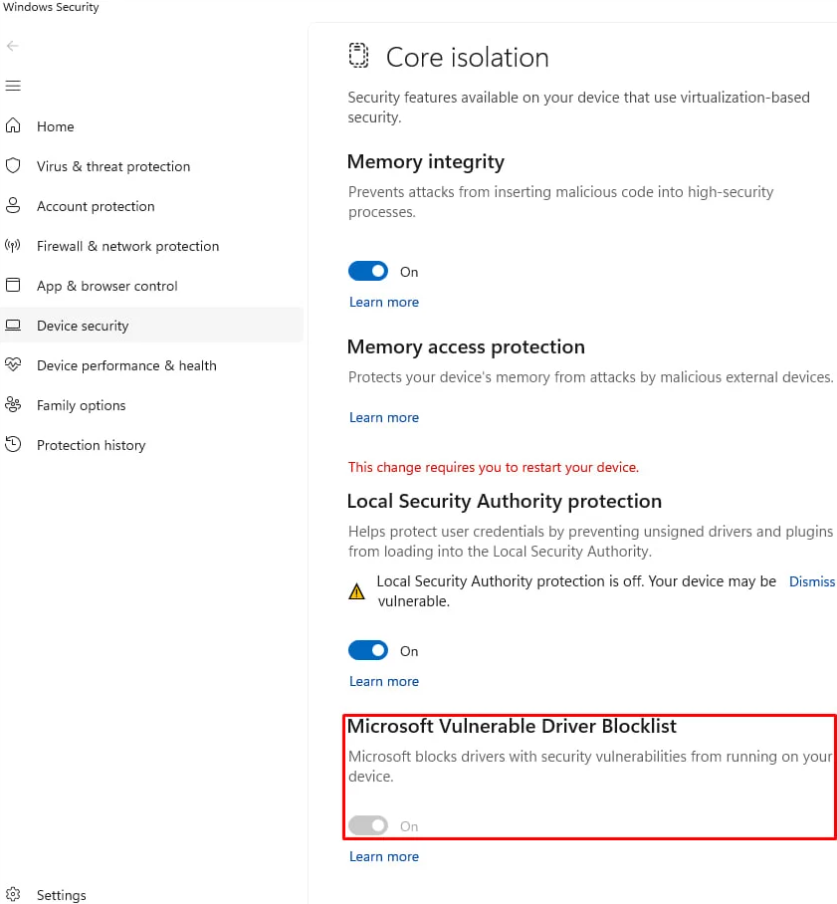
Disabling the Microsoft Vulnerable Driver Blocklist option will leave your device vulnerable to attacks through exploitable drivers.
To minimize risk, Microsoft recommends users upgrade their software to the latest version, which includes the fixed BioNTdrv.sys 2.0.0. In addition to updating the software, users should also check and enable Microsoft's Vulnerable Driver Blocking List by going to Settings > Privacy and Security > Windows Security > Device Security > Core Isolation > Microsoft Vulnerable Driver Blocking List and ensuring this feature is enabled.
Source: https://thanhnien.vn/microsoft-canh-bao-lo-hong-bao-mat-cua-phan-mem-quan-ly-o-dia-tren-windows-185250304165924709.htm














































































































Comment (0)