WinRAR, a popular file compression and decompression tool used on hundreds of millions of computers, is being targeted by hackers after a serious zero-day RCE (remote code execution) vulnerability was sold on the black market for up to $80,000.
The scary thing here is: this vulnerability is not a copy of an old, previously published vulnerability (CVE-2025-6218) but a completely new threat, unknown to anyone, with no patch, and still quietly existing in WinRAR versions from old to new.
One click, the whole system is in danger
This vulnerability allows an attacker to inject malicious code into the victim's system simply by… opening a "specially crafted" compressed file. No need to run the file, no need to grant permission, just double-clicking to unzip is enough for the hacker to take control.
Imagine you receive an email with a .rar file attached, and when you open it, it turns out to be... a birthday card or a contract. But in fact, in a split second, malware has been silently running in the background and breaking the security layer.

With WinRAR being widely used, from individual users to businesses, the price of 80,000 USD (more than 2 billion VND) for this vulnerability is not expensive, it is a "rare commodity" in the underground world, and almost guarantees that the attacks will not be detected.
Vulnerability from the platform
One thing to note: this security flaw affects multiple versions of WinRAR, not just the latest one. That suggests it’s likely an architectural flaw, not simply a sloppy coding error in a recent update.
WinRAR, because it has been around for decades and has many complex features, is a "fertile ground" for bad guys to exploit.
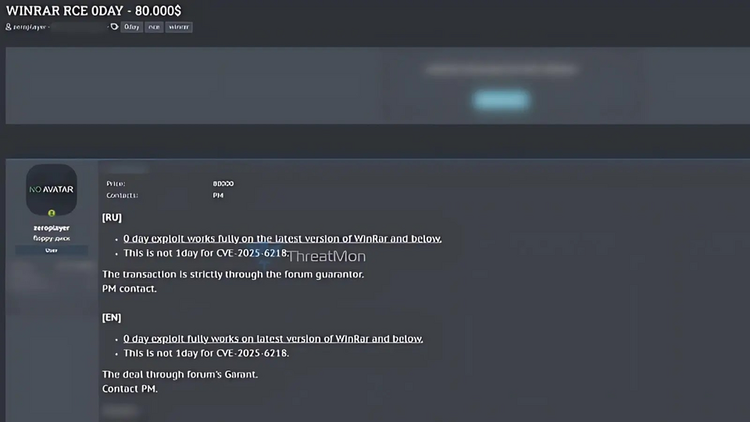
Security experts consider zero-day vulnerabilities like this a "security nightmare" because there are no signs of detection, no patches, and no traditional defenses that are effective enough. When the vulnerability is not yet public, users can only trust their fate.
What should users do?
While waiting for WinRAR developers to confirm and patch the bug, the best temporary prevention is to not open compressed files from unknown sources, especially from emails or strange links. Some emergency measures that can be applied:
- Use sandbox when opening compressed files
- Temporarily switch to another compression tool with better security controls
- Regularly update and monitor reputable security alert channels
Cybersecurity experts are closely monitoring this situation, because once the vulnerability is exploited in real-world attacks, the consequences will not stop at just a few infected computers.
Source: https://khoahocdoisong.vn/tin-tac-rao-ban-loi-zero-day-tren-winrar-voi-gia-2-ty-dong-post1555133.html



























































































![[Infographic] In 2025, 47 products will achieve national OCOP](https://vphoto.vietnam.vn/thumb/402x226/vietnam/resource/IMAGE/2025/7/16/5d672398b0744db3ab920e05db8e5b7d)





Comment (0)