Like any phishing attack, Darcula impersonates recognized entities to collect information from users. However, its attack method is quite sophisticated. While most previous types of attacks spread via SMS, Darcula uses the RCS communication standard.

Darcula is being spread by scammers in over 100 countries.
This is an uncommon attack method that has stumped both Google and Apple. This is because both Google Messages and iMessage use end-to-end encryption for messages. Due to this security mechanism, companies cannot block the threat based on its text content.
Darcula was first discovered last summer by security expert Oshri Kalfon. However, Netcraft reports that this phishing threat is becoming more prevalent recently and has been used in notable cases.
The methods used by Darcula are more complex than usual because they utilize modern technologies such as JavaScript, React, Docker, and Harbor. They have a library of over 200 website templates that impersonate brands or organizations in more than 100 countries. These impersonating website templates are high-quality and very similar to official websites.
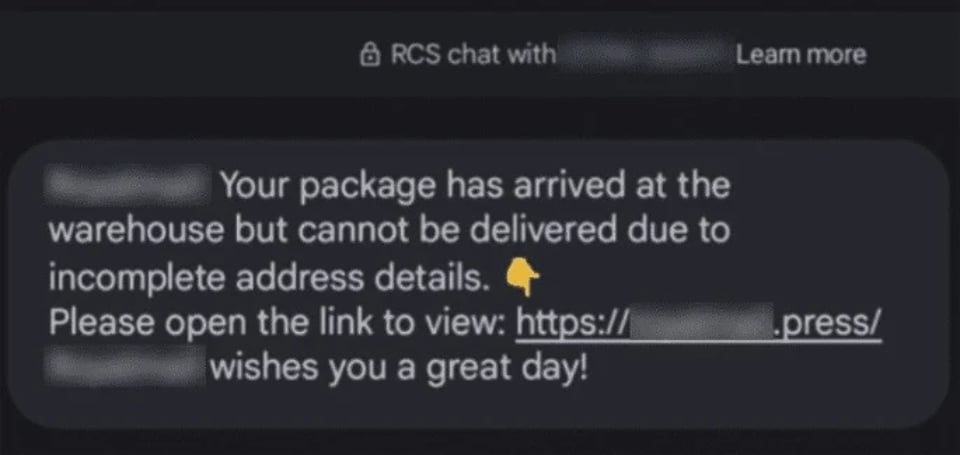
A message created by phishing attackers.
Darcula's modus operandi involves sending a link to the victim with incomplete message content and asking the recipient to visit their page for more details. Due to the high fidelity of these phishing websites, inexperienced users may provide them with data, which is then used for unknown purposes.
Netcraft claims to have detected 20,000 Darcula domain names transferred to over 11,000 IP addresses. The report also states that 120 new domain names are added daily, making identification even more difficult.
Given what has happened, users are advised to exercise greater caution when entering their personal data into sources provided via text messages, live calls, and unknown senders.
Source link



![[Photo] Standing Committee member of the Party Central Committee Tran Cam Tu presents the Decision appointing the Secretary of the Party Committee of the Ho Chi Minh National Academy of Politics.](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F1200x675%2Fvietnam%2Fresource%2FIMAGE%2F2026%2F02%2F02%2F1770039902160_le-cong-bo-bt-hvctqg-11-7880-jpg.webp&w=3840&q=75)



































































































![OCOP during Tet season: [Part 3] Ultra-thin rice paper takes off.](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F402x226%2Fvietnam%2Fresource%2FIMAGE%2F2026%2F01%2F28%2F1769562783429_004-194121_651-081010.jpeg&w=3840&q=75)







Comment (0)