This malware is capable of stealing photos and device information, then sending them to the hacker's server. SparkKitty often appears in applications related to cryptocurrency, betting games, and a fake version of TikTok. They are spread through the App Store, Google Play and also phishing websites. This attack campaign is said to target users in Southeast Asia and China, including Vietnam.
Kaspersky has warned Apple and Google about the malicious apps involved. Some details show that SparkKitty is related to SparkCat – a malware that has attracted attention for using OCR technology to scan screenshots to find passwords or recovery phrases for cryptocurrency wallets. This is the second time this year that experts have recorded a data-stealing Trojan appearing on the App Store.
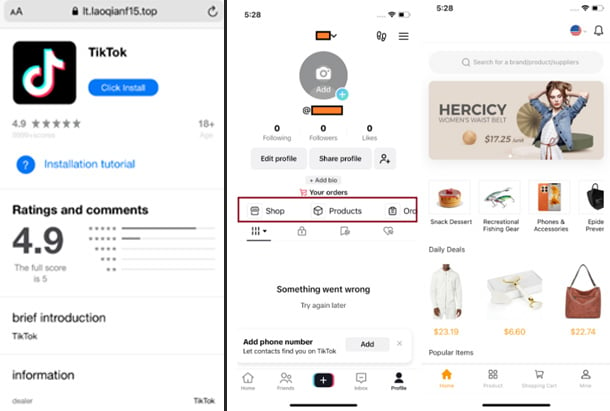
A fake App Store website that tricks users into installing the TikTok app, and a fake online store embedded in the fake TikTok app
On iOS, SparkKitty is disguised as 币coin, a cryptocurrency app. Additionally, fake App Store websites are spreading malware-infected versions of TikTok and gambling games. Hackers are using a developer tool to install the app outside the legitimate App Store. When users log in to the fake TikTok, the malware immediately accesses their photo library and places a malicious link in their profile – leading to a store that only accepts cryptocurrency payments.
Kaspersky expert Sergey Puzan warned: “The misuse of developer tools to spread malware is a worrying trend, as it bypasses iOS protection barriers. In particular, phishing websites are becoming more and more sophisticated, making it easy for users to be tricked into installing the wrong code.”

Fake SOEX Cryptocurrency Exchange App on Google Play
For Android, SparkKitty is also distributed via Google Play and external websites, hidden in cryptocurrency apps. One example is SOEX, a messaging app with integrated cryptocurrency trading functionality, which has had more than 10,000 downloads. In addition, third-party APK files also contain malicious code, which are heavily promoted on social networks such as YouTube, TikTok, and Facebook.
“The malware works invisibly, sending images to the attack server. These images can contain recovery keys for cryptocurrency wallets, allowing hackers to steal assets,” said expert Dmitry Kalinin. The fact that most of the infected apps are related to cryptocurrencies suggests that the main goal is to steal digital assets.
Users are advised not to install applications from untrusted sources, carefully check developer information and use mobile security solutions.
A detailed report on this attack campaign is posted on Securelist.com.
Source: https://nld.com.vn/canh-bao-trojan-sparkkitty-gia-mao-tiktok-tan-cong-nguoi-dung-ios-va-android-196250627073413671.htm





![[Photo] Prime Minister Pham Minh Chinh attends a conference to review one year of deploying forces to participate in protecting security and order at the grassroots level.](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/11/12/1762957553775_dsc-2379-jpg.webp)

![[Photo] The "scars" of Da Nang's mountains and forests after storms and floods](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/11/13/1762996564834_sl8-jpg.webp)
















![[INFOGRAPHIC] Who is the former Mayor of Istanbul facing a 2,430-year prison sentence?](https://vphoto.vietnam.vn/thumb/402x226/vietnam/resource/IMAGE/2025/11/13/1762996572530_info-tt-istanbul-anh-thumb-jpg.webp)












![[Photo] Highways passing through Dong Nai](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/11/12/1762940149627_ndo_br_1-resize-5756-jpg.webp)



































































![Dong Nai OCOP transition: [Article 3] Linking tourism with OCOP product consumption](https://vphoto.vietnam.vn/thumb/402x226/vietnam/resource/IMAGE/2025/11/10/1762739199309_1324-2740-7_n-162543_981.jpeg)








Comment (0)