 |
A malware was discovered on a Samsung smartphone. Photo: Dailyrecord . |
Researchers at Unit 42, the threat intelligence arm of Palo Alto Networks, have revealed a sophisticated spyware called “Landfall” that targets Samsung Galaxy phones.
The campaign, which exploited a zero-day vulnerability in Samsung's Android software to steal vast amounts of personal data, has been active for nearly a year, according to researchers. The vulnerability has now been patched, and the attacks appear to be targeting specific groups.
Unit 42 said Landfall first appeared in July 2024, recorded with the identifier CVE-2025-21042. Samsung released a patch for its devices in April 2025, but details of the attack were only recently released.
The team believes Landfall is being used in the Middle East to track specific individuals, so the chances of infection before the patch are released are low. It is still unclear who is behind these attacks.
Landfall is particularly dangerous because it is a “zero-click” attack, meaning it can penetrate a system without any user action. Unit 42 discovered it only after noticing two similar bugs that had been patched in Apple iOS and WhatsApp.
Combined, the two vulnerabilities could allow remote code execution, so the team began looking for similar exploits. They discovered multiple malicious image files uploaded to VirusTotal, a service that scans suspicious files and links, revealing traces of the Landfall attack.
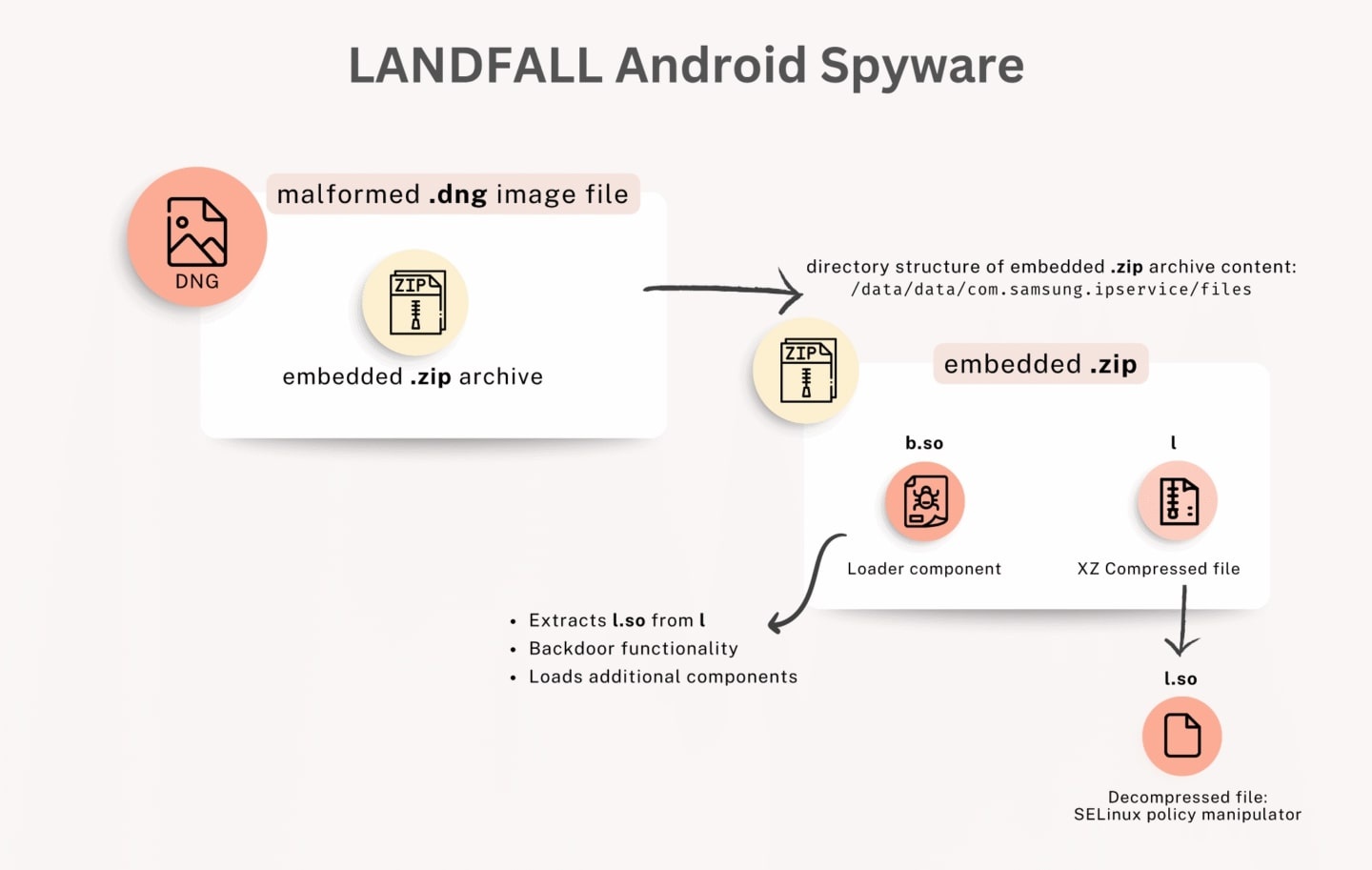 |
How Landfall works. Photo: Unit 42. |
Typically, image files cannot execute code, but some can be modified to contain malicious code. In the Landfall case, the attackers used DNG files, a raw image file format based on the TIFF format, with ZIP files embedded inside containing malicious code.
Before the patch, Samsung phones had a vulnerability in the image processing library. The malicious image processing system for display would unpack shared library files from ZIP files and inadvertently run the Landfall spyware.
The malware also modifies the device's SELinux policy to steal extended permissions and access data. Unit 42 notes that the malware references specific Samsung phone models, including the Galaxy S22, S23, S24, Z Flip4, and Z Fold4.
Once active, Landfall contacts a remote server that sends basic information about the device. Operators can then extract a wealth of data, such as user and hardware IDs, installed apps, contacts, any files stored on the device, and browsing history, and potentially activate the camera and microphone to spy on the user.
Removing the spyware is not easy either. Because of its ability to interfere with SELinux policies, Landfall can penetrate deeply into the system and is equipped with many tools to avoid detection.
Based on files uploaded to VirusTotal, the Unit 42 team believes Landfall was active in 2024 and early 2025, primarily in Iraq, Iran, Turkey, and Morocco. According to Samsung, the vulnerability may exist in its software from Android 13 to Android 15.
While this attack was very narrow in scope and clearly targeted, the technical details are now public, meaning that other attackers could potentially use the same method to compromise unpatched devices. Samsung users should therefore ensure their devices are updated to the April 2025 patch or later.
Source: https://znews.vn/ma-doc-dac-biet-nguy-hiem-nam-tren-smartphone-samsung-ca-nam-post1601170.html


































































































Comment (0)