According to Sophos research, over 56% of businesses were attacked by this malware, and 70% had their data encrypted, with ransom demands increasing fivefold compared to 2023.
Ransomware targets businesses.
The State of Ransomware 2024 special report from Sophos, which details the current state of ransomware, shows that 2024 continues to be a 'disastrous' year for businesses due to relentless ransomware attacks.
According to Sophos, cyberattacks targeting small and medium-sized enterprises (SMEs) continue to increase. Ransomware, in particular, is considered a major threat to businesses of all sizes. These attacks are becoming increasingly frequent and serious, with ransom demands reaching tens of millions of dollars or causing equivalent losses due to operational disruptions. In addition, advanced persistent threats (APTs) remain a major threat to all organizations and businesses.
Ransomware is a term used to describe malware that encrypts a victim's data, seizes it, and demands a ransom. Hackers demand that victims, often businesses, pay a ransom in cryptocurrency such as Bitcoin to 'rescue' their data.
According to Sophos, more than half of medium- and large-sized businesses from 14 countries reported being attacked by ransomware in 2024. The vulnerabilities most heavily exploited by ransomware included software or system security flaws (32%), attacks on weak points (29%), malicious emails (23%), and targeted phishing (11%). On average, 35% of businesses took a week to restore operations disrupted by a ransomware attack, while 34% took a month.
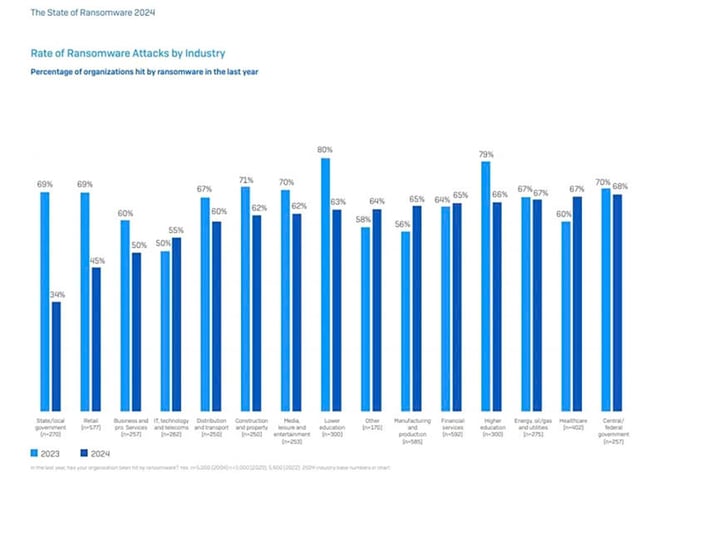
The chart compares the rate of ransomware attacks on industrial and commercial sectors, and management and government organizations. Healthcare organizations and hospitals remain the most targeted, accounting for 68%.
Lack of a unified solution
According to Sophos, the reason enterprise systems are vulnerable to intrusion attacks is due to the overlap of software, especially in the era of AI (artificial intelligence).
The development of new technologies applied to the operations of all organizations and businesses has increased the surface area for cyberattacks. Too many security vulnerabilities from applications and operating systems are regularly disclosed, and IT administrators have not kept up, creating opportunities for cybercriminals to carry out attacks.

Many security vulnerabilities originate from applications and operating systems.
According to a Sophos representative, the complexity of IT systems is the reason why most organizations and businesses are facing numerous security and information safety issues. Three main problems include: many "blind spots" in the implementation of security solutions; a lack of monitoring tools to allow administrators to see the entire system; and a shortage of highly skilled personnel to operate and handle information security incidents.
Sophos suggests that small and medium-sized enterprises (SMEs) that lack a professional workforce can use professional solutions to overcome these weaknesses.
Sophos offers Sophos EDR and XDR (Early Detection and Response) solutions with key advantages: Early detection of 'hidden', unnoticed attacks; Reliable security status reports at any given time; Rapid response and optimal incident handling; Operators gain a better understanding of the attack that occurred and how to prevent it. This provides businesses with a 24/7 security expert.
According to experts from Sophos, a robust Endpoint Protection Platform (EPP) is insufficient to prevent increasingly sophisticated malware attacks. Therefore, advanced technologies are being applied to help EPPs detect and respond effectively to such incidents, namely Endpoint Detection & Response (EDR). XDR is an extension of EDR.
Sophos XDR can help detect and respond to any incidents originating from workstations, servers, firewalls, mobile devices, the cloud, and more.
Three features give Sophos EDR and XDR an advantage:
Live Discovery allows administrators to search and query all information about the system's status, malware, attacks, etc., using historical data stored in the Data Lake. It supports proactive IT threat hunting based on indicators of attack (IoA) and indicators of compromise (IoC).
Live Response: guides administrators on how to effectively respond to incidents, including actions such as: Isolation, Quarantine, Scanning, Sampling or in-depth analysis of malicious objects (getting files, creating threat cases), etc. Administrators will have remote access to the endpoint via the administration interface for quick response.
Threat Intelligence: Provides a hierarchical, interconnected root cause analysis of events and incidents. Integrates advanced technologies such as AI, ML/DL (Machine Learning), Cloud Sandboxing, etc., to analyze suspicious files and generate detailed reports on those objects.
Source


![[Image] Leaked images ahead of the 2025 Community Action Awards gala.](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F1200x675%2Fvietnam%2Fresource%2FIMAGE%2F2025%2F12%2F16%2F1765882828720_ndo_br_thiet-ke-chua-co-ten-45-png.webp&w=3840&q=75)

![[Photo] Prime Minister Pham Minh Chinh receives Lao Minister of Education and Sports Thongsalith Mangnormek](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F1200x675%2Fvietnam%2Fresource%2FIMAGE%2F2025%2F12%2F16%2F1765876834721_dsc-7519-jpg.webp&w=3840&q=75)
![[Photo] Prime Minister Pham Minh Chinh receives the Governor of Tochigi Province (Japan)](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F1200x675%2Fvietnam%2Fresource%2FIMAGE%2F2025%2F12%2F16%2F1765892133176_dsc-8082-6425-jpg.webp&w=3840&q=75)
![[Live] 2025 Community Action Awards Gala](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F1200x675%2Fvietnam%2Fresource%2FIMAGE%2F2025%2F12%2F16%2F1765899631650_ndo_tr_z7334013144784-9f9fe10a6d63584c85aff40f2957c250-jpg.webp&w=3840&q=75)




























































![[Video] Independence and self-reliance linked with international integration through 40 years of reform](https://vphoto.vietnam.vn/thumb/402x226/vietnam/resource/IMAGE/2025/12/16/1765899635777_1-1-8054-png.webp)





































Comment (0)