On June 26, experts from Kaspersky announced that they had discovered a new spyware called SparkKitty, designed to attack smartphones using iOS and Android operating systems, then send images and device information from infected phones to the attacker's server.
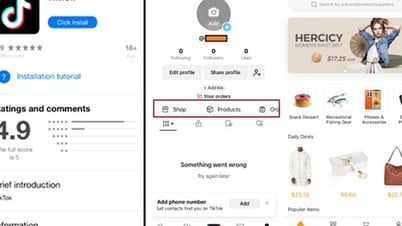
SparkKitty was embedded in apps with content related to cryptocurrencies, gambling, as well as in a fake version of the TikTok app. These apps were distributed not only through the App Store and Google Play, but also on fraudulent websites.
According to experts' analysis, the goal of this campaign may be to steal cryptocurrency from users in Southeast Asia and China. Users in Vietnam are also at risk of facing similar threats.
Kaspersky has notified Google and Apple to take action against the malicious apps. Some technical details suggest that the new campaign is linked to SparkCat, a Trojan previously discovered. SparkCat is the first malware on the iOS platform with a built-in optical character recognition (OCR) module that scans users' photo libraries and steals screenshots containing passwords or recovery phrases for cryptocurrency wallets.
After SparkCat, this is the second time this year that Kaspersky researchers have discovered a Trojan stealer on the App Store.
On the App Store, this Trojan malware is disguised as a cryptocurrency-related application called 币coin. In addition, on fraudulent websites designed to mimic the iPhone App Store interface, cybercriminals also spread this malware under the guise of the TikTok application and some betting games.
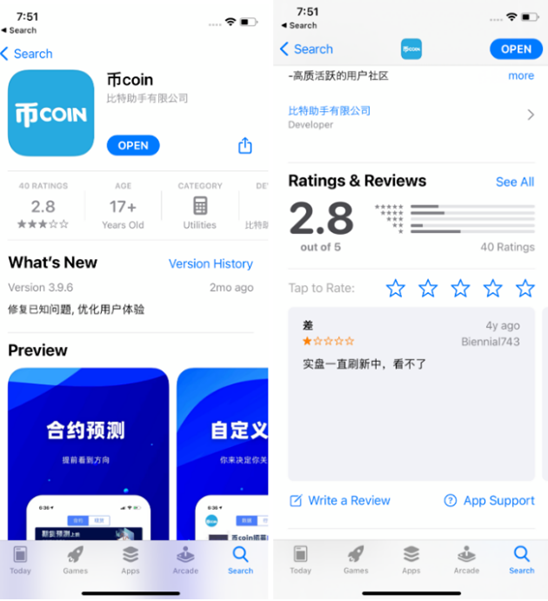
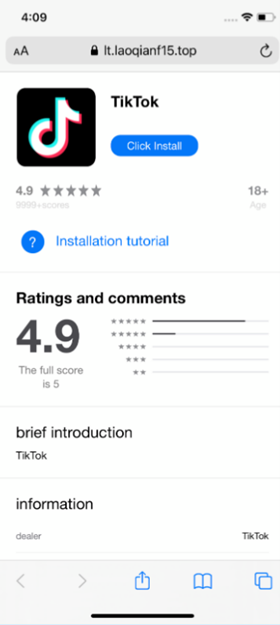
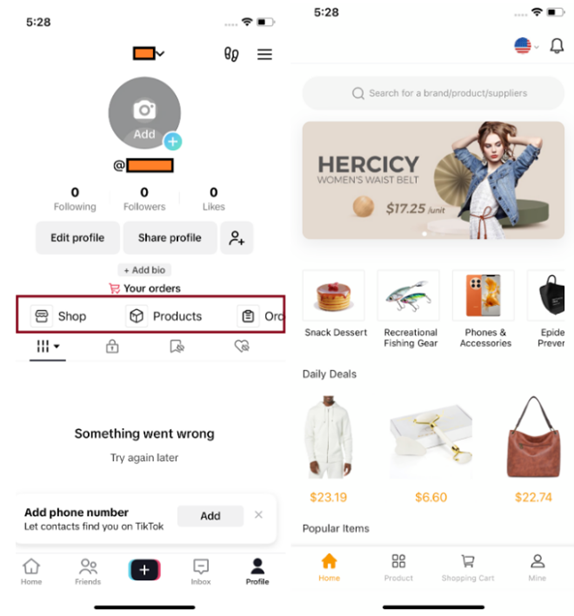
“Fake websites are one of the most popular channels for distributing Trojans, where hackers try to trick users into visiting and installing malware on iPhones. On iOS, there are still some legitimate ways for users to install apps from outside the App Store. In this attack, hackers took advantage of a developer tool designed to install internal apps within businesses. In the infected version of TikTok, as soon as the user logs in, the malware steals photos from the phone’s gallery and secretly inserts a strange link into the victim’s personal page. What’s worrying is that this link leads to a store that only accepts cryptocurrency payments, which makes us even more concerned about this campaign,” said Sergey Puzan, malware analyst at Kaspersky.
On Android, attackers targeted users on both Google Play and third-party websites by disguising the malware as cryptocurrency-related services. One example of an infected app is SOEX, a messaging app with built-in cryptocurrency trading functionality, with over 10,000 downloads from the official store.

In addition, experts also discovered APK files (Android application installation files, which can be installed directly without going through Google Play) of these malware-infected applications on third-party websites, believed to be related to the above attack campaign.
These apps are promoted under the guise of cryptocurrency investment projects. Notably, the websites that distribute the apps are also widely promoted on social networks, including YouTube.
“Once installed, the apps function as described. However, during installation, they silently infiltrate the device and automatically send images from the victim’s gallery back to the attacker. These images may contain sensitive information that the hackers are looking for, such as crypto wallet recovery scripts, allowing them to steal the victim’s digital assets,” said Dmitry Kalinin, a malware analyst at Kaspersky. “There are indirect signs that the attackers are after users’ digital assets: many of the infected apps are related to cryptocurrencies, and the infected version of TikTok also includes a store that only accepts cryptocurrency payments.”
To avoid falling victim to this malware, Kaspersky recommends users take the following safety measures:
- If you have accidentally installed one of the infected applications, quickly remove the application from your device and do not use it again until there is an official update to completely remove the malicious feature.
- Avoid storing screenshots containing sensitive information in your photo library, especially images containing cryptocurrency wallet recovery codes. Instead, users can store login information in dedicated password management applications.
- Install reliable security software to prevent the risk of malware infection. For iOS operating systems with their unique security architecture, Kaspersky's solution will warn if it detects a device transmitting data to a hacker's control server and block this data transmission process.
- When an application requests access to the photo library, users should carefully consider whether this permission is really necessary for the application's main function./.
Source: https://www.vietnamplus.vn/phat-hien-phan-mem-gian-diep-moi-nham-vao-nguoi-tren-app-store-va-google-play-post1046585.vnp





































![[Photo] General Secretary To Lam and National Assembly Chairman Tran Thanh Man attend the 80th Anniversary of the Traditional Day of the Vietnamese Inspection Sector](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/11/17/1763356362984_a2-bnd-7940-3561-jpg.webp)















































































Comment (0)