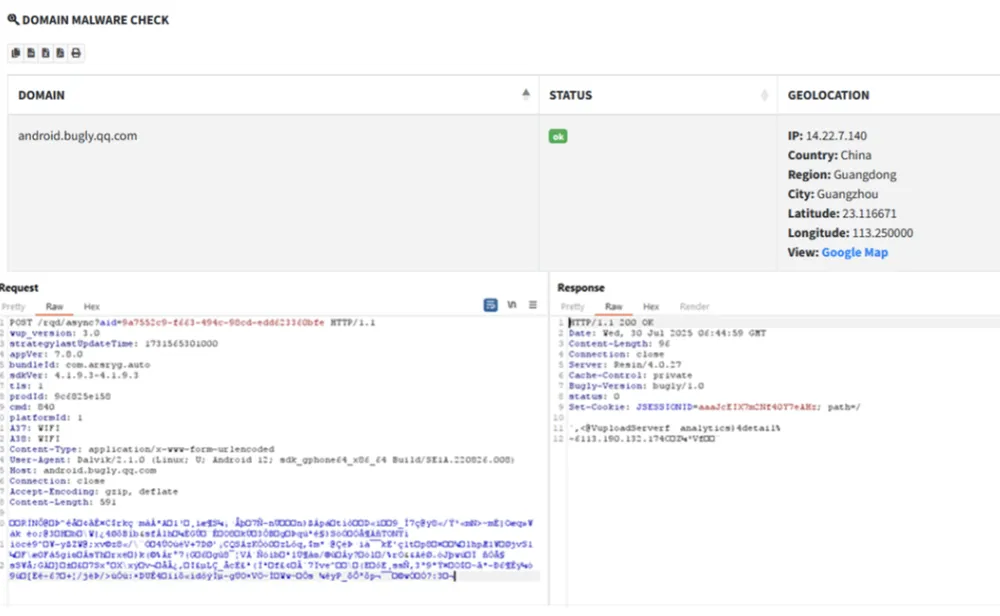
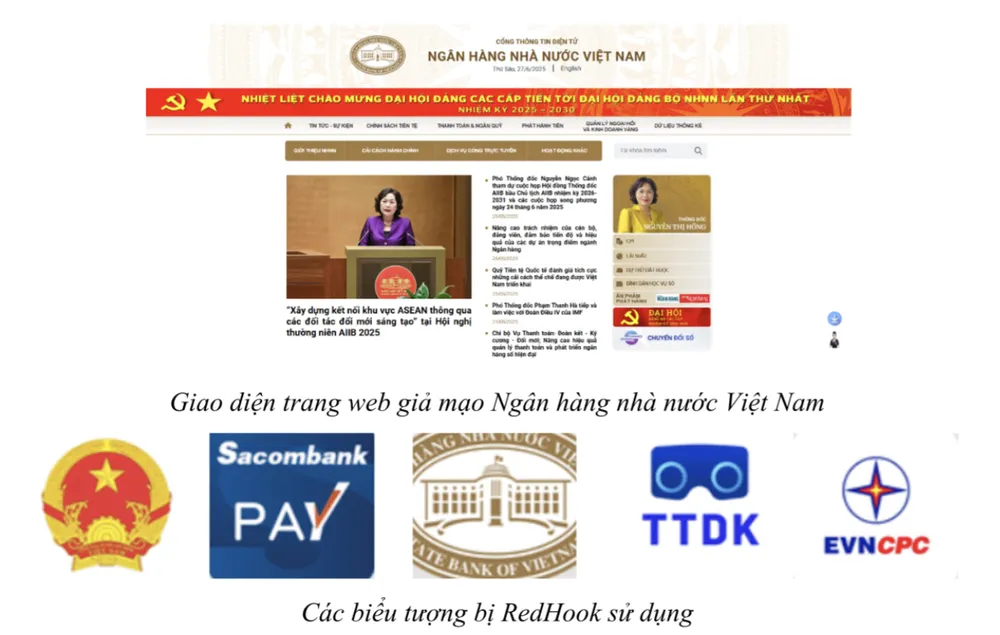
Hackers create fake websites of state agencies or reputable financial institutions such as: State Bank of Vietnam (SBV), Sacombank (Sacombank Pay), Central Power Corporation (EVNCPC), Automobile Inspection Appointment System (TTDK)... install malware under the guise of applications, then trick users into downloading them to their phones, using many different scenarios such as sending emails, texting via chat applications or running ads on search engines...
The fake app is disguised with the same name as the real app, just with a different extension (e.g. SBV.apk) and is stored on the Amazon S3 cloud, making it easy for hackers to update, change and hide malicious content. Once installed, the fake app asks the user to grant deep access to the system, including Accessibility and Overlay permissions.
Combining these two rights, hackers can monitor user operations, read SMS message content, get OTP codes, access contacts, and even operate on behalf of users without leaving any obvious signs.
By decompiling the source code of RedHook, experts from Bkav's Malware Analysis Center discovered that this virus integrates up to 34 remote control commands, including taking screenshots, sending and receiving messages, installing or uninstalling applications, locking and unlocking devices, and executing system commands. They use the MediaProjection API to record all content displayed on the device screen and then transfer it to the control server.
RedHook has a JSON Web Token (JWT) authentication mechanism, which helps attackers maintain control of the device for a long time, even when the device is rebooted.
During the analysis process, Bkav discovered many code segments and interface strings using Chinese language along with many other clear traces of the hacker group's development origin as well as the RedHook distribution campaign related to fraudulent activities that have appeared in Vietnam.
For example, the use of the domain name mailisa[.]me, a popular beauty service that has been exploited in the past, to spread malware shows that RedHook is not operating alone but is the product of a series of organized attack campaigns, which are sophisticated in both technical and tactical aspects. The control server domains used in this campaign include api9.iosgaxx423.xyz and skt9.iosgaxx423.xyz, both of which are anonymous addresses located overseas and cannot be easily traced.
Bkav recommends that users absolutely do not install applications outside of Google Play, especially APK files received via text messages, emails or social networks. Do not grant accessibility rights to applications of unknown origin. Organizations need to deploy access monitoring measures, DNS filtering and set up warnings for connections to unusual domains related to the malware's control infrastructure. If you suspect an infection, immediately disconnect from the Internet, back up important data, restore factory settings (factory reset), change all account passwords, and contact the bank to check the account status.
Source: https://www.sggp.org.vn/dien-thoai-android-tai-viet-nam-dang-bi-tan-cong-co-chu-dich-post807230.html


![[Photo] Closing of the 14th Conference of the 13th Party Central Committee](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/11/06/1762404919012_a1-bnd-5975-5183-jpg.webp)







































































































Comment (0)