 |
There is a new cyber attack campaign targeting businesses in Vietnam. Illustration photo: Bloomberg. |
Security researchers at SEQRITE Labs have discovered a sophisticated cyberattack campaign. Dubbed “Operation Hanoi Thief”, the campaign targets IT departments and recruitment agencies in Vietnam by disguising CVs.
First discovered on November 3, hackers used the technique of spreading malware by disguising it as a job application CV. The attackers' goal was to infiltrate the internal network, take over the system and steal customer data and business secrets.
How malware works
According to security experts, the attacker sent a series of emails with job applications, attaching the file “Le Xuan Son CV.zip”. When unzipped, it contained two files, one named “CV.pdf.lnk”, the other named “offsec-certified-professional.png”.
Because it is disguised as a PDF and PNG icon, users may mistake this for a normal CV file. When clicked, the file will activate the LOTUSHARVEST virus, which specializes in collecting password information, access history... and then sending it to the hacker's server.
According to GBHackers , the fake CV named Le Xuan Son from Hanoi has had a GitHub account since 2021. However, researchers discovered that this account did not post any information, most likely just to serve the attack campaign.
The attack proceeds in three stages. After opening the LNK file, it triggers a special command via the ftp.exe tool built into Windows. This is an old and no longer common technique that allows the malware to bypass basic controls.
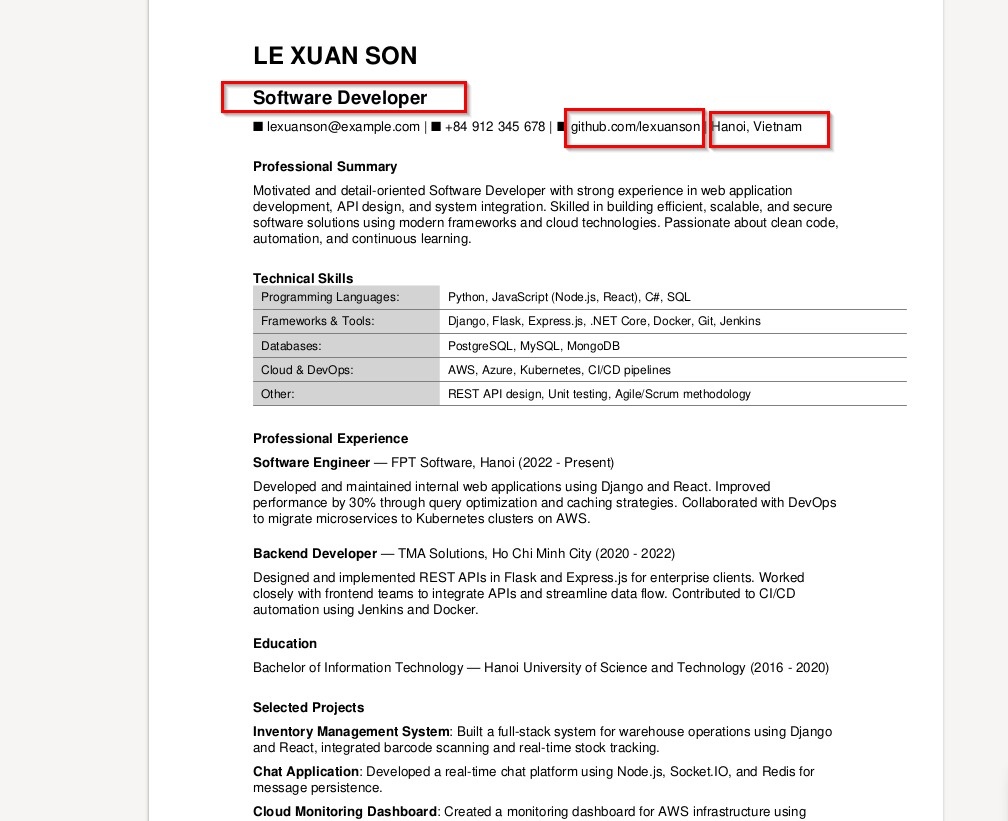 |
Hackers trick businesses by sending CVs under the name "Le Xuan Son". Photo: SEQRITE . |
In phase 2, the system is still fooled into thinking this is a PDF or plain text file. However, upon further analysis, the researchers discovered that the malicious code was inserted hidden before the beginning of the PDF file.
The malware immediately went to work, renaming the certutil.exe tool available in Windows to avoid detection, and extracting the data containing the final malicious file package. The command line continued to rename the file to “CV-Nguyen-Van-A.pdf” to fool the system, then extracted and decrypted a file named “MsCtfMonitor.dll”, placing it in the C:\ProgramData folder.
By copying the ctfmon.exe file from System32 to the same folder, the attacker exploited the DLL hijacking technique, causing the system to run the malicious file instead of the normal program.
Finally, the LOTUSHARVEST malware is activated to steal information. This data includes login information on Chrome and Edge browsers, along with the 20 most recently visited URLs, including related metadata.
The stolen data is transmitted through Windows' WinINet API to the hacker's infrastructure. The software also adds the computer name and username to create an identity profile on the server.
Vietnamese businesses need to strengthen protection
The worrying point in the attack campaign is that LOTUSHARVEST has the ability to hide itself and operate on its own. The malware takes advantage of the library loading mechanism to maintain long-term control and access sensitive accounts and data, beyond the protection of conventional security measures.
According to the assessment, stolen data can become the "key" for hackers to expand their penetration, deploy dangerous tools and turn businesses into targets of multi-layer attacks or extortion in the next stages.
“Every indication is that the Hanoi Thief campaign was meticulously planned, targeting Vietnamese businesses directly.
Taking advantage of the recruitment department, which regularly receives applications from outside but is not fully equipped with cybersecurity awareness, hackers use fake files in the form of CVs or documents and can continuously transform into many variations, making the risk of infection unpredictable," said Mr. Nguyen Dinh Thuy, Malware Analysis Expert at Bkav.
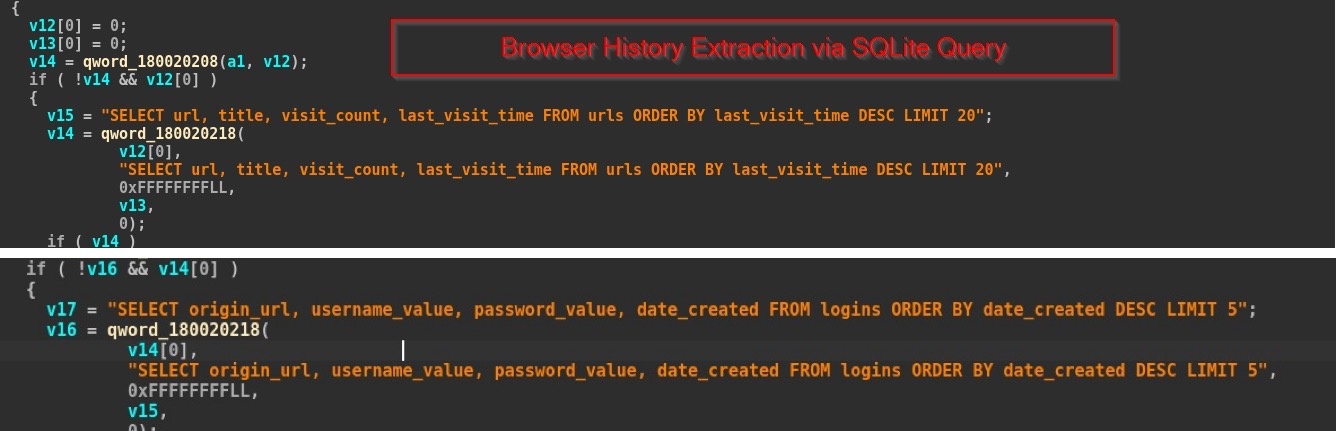 |
The scripts extract the malware's login and access history. Photo: SEQRITE . |
According to Bkav, there are Vietnamese enterprises that have become victims of the attack campaign. Due to the dangerous nature of LOTUSHARVEST and the Hanoi Thief campaign, users need to be extremely vigilant with documents received via email.
Businesses and organizations need to regularly conduct periodic training for employees, raise awareness and vigilance against online fraud tricks. Internal monitoring systems need to be strengthened, monitoring unusual libraries or suspicious files.
The default tools on the operating system only meet basic protection needs, not enough to fight against modern malware and viruses that can hide, persist for a long time and penetrate deeply into the system. Therefore, it is necessary to install an email monitoring system and use licensed anti-virus software for the best protection.
Source: https://znews.vn/canh-giac-khi-mo-cv-xin-viec-cua-le-xuan-son-post1608612.html







![[Photo] Cat Ba - Green island paradise](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F1200x675%2Fvietnam%2Fresource%2FIMAGE%2F2025%2F12%2F04%2F1764821844074_ndo_br_1-dcbthienduongxanh638-jpg.webp&w=3840&q=75)





























































































Comment (0)